With smart medical devices and other Internet of Things (IoT) technologies becoming staples in healthcare, boosting IoT security is more critical than ...
Xact IT Solutions
MACI PRONTO

How to protect healthcare IoT devices from cyberthreats
Xact IT Solutions
XACT IT SOLUTIONS INC

CrushFTP Vulnerability CVE-2025-31161: What It Means for Your Business and How to Respond
In the fast-paced world of cybersecurity, staying informed and proactive isn’t optional — it’s essential. Over the past week, a newly discovered ...
Xact IT Solutions
XACT IT SOLUTIONS INC

NASCAR Targeted in Alleged Medusa Ransomware Attack: A Wake-Up Call for All Businesses
In a significant development that underscores the growing threat of cybercrime, the infamous Medusa ransomware group has allegedly claimed responsibility ...
Xact IT Solutions
MACI PRONTO

How emerging tech is rewriting the rules of data security
Data breaches are an unfortunate norm in today’s digital world, and traditional encryption techniques are no longer enough to prevent them. In addition, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Critical SQL Injection Vulnerability in Halo ITSM, PSA & CRM – Patch Now to Prevent Exploits
Organizations using Halo’s ITSM, PSA, or CRM platforms are being urged to take immediate action after cybersecurity researchers uncovered a critical ...
Xact IT Solutions
XACT IT SOLUTIONS INC

How Hackers Steal Data in Under 5 Hours — What Your Business Must Know
In today’s digital landscape, cybercriminals are no longer relying solely on traditional ransomware tactics. Instead, they’re moving with unprecedented ...
Xact IT Solutions
MACI PRONTO

Stop replacing, start maintaining: Tips for business hardware longevity
Don’t let dust, disorganization, or neglect shorten the life of your devices. Follow these practical tips to protect your tech investments, maximize ...
Xact IT Solutions
MACI PRONTO

Enhance communications with these Skype substitutes in 2025
The familiar blue icon of Skype has been a staple for online conversations for years. However, with Microsoft set to retire the platform on May 5, 2025, ...
Xact IT Solutions
MACI PRONTO

Increasing business efficiency with Microsoft 365 Copilot AI agents
AI (artificial intelligence) has come a long way from its early days of powering chatbots and automated emails. With Microsoft’s new Copilot Studio, ...
Xact IT Solutions
MACI PRONTO

How AI is changing workplace surveillance
Companies are always looking for new ways to boost productivity, and artificial intelligence (AI) has become a key tool in achieving this goal. AI-powered ...
Xact IT Solutions
XACT IT SOLUTIONS INC
The Hidden Costs of Handling CMMC Compliance In-House
For many government contractors, achieving Cybersecurity Maturity Model Certification (CMMC) compliance is a critical step in securing DoD contracts. ...
Xact IT Solutions
MACI PRONTO

What developers should focus on to strengthen software security
A recent analysis of the most damaging software attacks revealed that many cybersecurity guides overlook critical protections, leaving systems exposed ...
Xact IT Solutions
MACI PRONTO

Activate Siri on macOS without giving Apple access to your contacts
Mac users love the convenience of Siri for performing quick tasks or finding information. However, enabling Siri on macOS often comes with a privacy ...
Xact IT Solutions
MACI PRONTO

The future is unified: UCaaS and CCaaS convergence for SMB success
The line between employee communication tools and customer service platforms is starting to blur — and that’s a good thing. For small and mid-sized ...
Xact IT Solutions
MACI PRONTO

Windows 10 is nearing its end of life — here’s what you need to know
Microsoft will officially cease support for Windows 10 in October 2025, marking the end of an era for one of the most widely used operating systems. ...
Xact IT Solutions
MACI PRONTO

How your web browser keeps you one step ahead of cyberthreats
When it comes to online safety, HTTPS (Hypertext Transfer Protocol Secure) is your first line of defense. In this article, we explore how HTTPS helps ...
Xact IT Solutions
MACI PRONTO

Protecting patient data: Why HIPAA matters to your healthcare business
If your company operates in the healthcare industry or works with related organizations, you’re likely familiar with the Health Insurance Portability ...
Xact IT Solutions
MACI PRONTO

What to prioritize when choosing computer hardware for your business
With an overwhelming number of options on the market, choosing the right computer hardware for your business can feel like a daunting task. The challenge ...
Xact IT Solutions
MACI PRONTO

The state of ransomware in 2025: What businesses need to know
Ransomware has become a significant hazard to enterprises globally, with attackers evolving their methods to cause more disruption and demand higher ...
Xact IT Solutions
MACI PRONTO

VoIP bandwidth requirements and tips for clear business calls
If you’re switching to Voice over Internet Protocol (VoIP), you might wonder if your internet bandwidth is up to the task. While VoIP doesn’t use ...
Xact IT Solutions
MACI PRONTO

Harnessing the full potential of Microsoft Copilot
Microsoft Copilot and other AI tools are changing how people work, research, and create. But are you using these tools to their full potential? This ...
Xact IT Solutions
MACI PRONTO

Why your cloud costs are skyrocketing — and how to get them under control
Cloud computing offers scalability and flexibility, but many organizations are burdened with unexpectedly high expenses. Read this article to understand ...
Xact IT Solutions
MACI PRONTO

Why SMBs need regular technology business reviews
Technology is always evolving, and for small or mid-sized businesses like yours, staying ahead means taking a close look at your IT strategy. A technology ...
Xact IT Solutions
MACI PRONTO

Password managers under attack: Protect your SMB
Many small or medium-sized businesses (SMBs) rely on password managers to simplify and secure their authentication processes, but these tools are now ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Why Ransomware Payments Dropped in 2024 – But Attacks Are Still Rising
Ransomware is one of the most persistent cybersecurity threats, and recent reports suggest that ransomware payments have significantly declined in 2024. ...
Xact IT Solutions
XACT IT SOLUTIONS INC

The Deep Seek Breach: What It Means for AI Security and Your Business
In the fast-moving world of artificial intelligence, security is often overlooked—until something goes wrong. Recently, a cybersecurity breach involving ...
Xact IT Solutions
MACI PRONTO

How to manage Apple devices in your business
Apple devices are popular in business settings for their reliability and security, but managing a fleet of Macs, iPads, and iPhones can be challenging. ...
Xact IT Solutions
MACI PRONTO

Seamless cloud UC migration: A practical guide for businesses
Transferring your unified communications (UC) system to the cloud unlocks enhanced flexibility, broad accessibility, and simplified management. However, ...
Xact IT Solutions
MACI PRONTO

Windows PowerToys: The ultimate productivity boost for your PC
Microsoft has revamped PowerToys, its collection of free utilities designed to supercharge your Windows experience. Whether you need to resize images, ...
Xact IT Solutions
MACI PRONTO

Tips for protecting your computer from browser threats
Every time your employees browse the web — whether searching on Google or accessing work applications — they face potential cyberthreats like phishing ...
Xact IT Solutions
MACI PRONTO

AI’s secret superpower: Spotting diseases before symptoms even appear
Artificial intelligence (AI) is transforming disease detection, identifying health conditions doctors may not even be looking for. By analyzing medical ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Interim DFARS Rule: What It Means for DoD Contractors & How to Stay Compliant
The Cybersecurity Maturity Model Certification (CMMC) became part of the Defense Federal Acquisition Regulation Supplement (DFARS) in January 2020 and ...
Xact IT Solutions
MACI PRONTO

How to pick the right antivirus software for your SMB
When running a small or medium-sized business (SMB), security should never be an afterthought. With cyberattacks becoming more advanced, having reliable ...
Xact IT Solutions
MACI PRONTO

Reduce IT spending with thin and zero clients
Is your IT budget eating into your company’s profits? Traditional desktop setups come with hidden costs that add up over time. Fortunately, businesses ...
Xact IT Solutions
MACI PRONTO

How 5G is revolutionizing VoIP: A quick guide
Ready to take your business’s VoIP (Voice over Internet Protocol) experience to the next level? Enter 5G — a technology that’s redefining how we ...
Xact IT Solutions
MACI PRONTO
Unlocking the full potential of Outlook in Microsoft 365
Managing your emails doesn’t need to be overwhelming. With Outlook in Microsoft 365, you can effortlessly organize your inbox, simplify scheduling, ...
Xact IT Solutions
MACI PRONTO

Video conferencing gives businesses a competitive edge in the hybrid era
Effective collaboration is essential in business, and for hybrid teams, video conferencing has become a mission-critical tool for collaborating. However, ...
Xact IT Solutions
MACI PRONTO

How business intelligence fuels success
Business intelligence (BI) is revolutionizing the way companies operate, specifically by providing deep insights that drive efficiency and growth. Businesses ...
Xact IT Solutions
MACI PRONTO

Watch out! These social engineering tricks could fool anyone
While it’s easy to blame cyberattacks on sophisticated hacking, the truth is that many attackers rely on social engineering — a craft of deception ...
Xact IT Solutions
MACI PRONTO

Why your business should start recording business calls
Every conversation in business carries value, whether it’s a sales pitch, a customer complaint, or an internal team discussion. Recording business ...
Xact IT Solutions
MACI PRONTO

How to disable AI in Windows and your browser
Microsoft and other tech companies have been integrating artificial intelligence (AI) into their products to make tasks easier and more efficient for ...
Xact IT Solutions
MACI PRONTO

Protect your hybrid work system’s communications portal from online threats
This article examines the challenges of maintaining data security while fostering a connected and engaged workforce in a hybrid or remote work environment. ...
Xact IT Solutions
MACI PRONTO

What’s next in healthcare IT? 4 Trends for 2025
Healthcare technology is advancing rapidly, and in 2025 we can expect even more groundbreaking developments. This year, AI-driven tools, cutting-edge ...
Xact IT Solutions
XACT IT SOLUTIONS INC
8 Common IT Support Problems Businesses Face and How to Fix Them
In today’s technology-driven world, businesses heavily depend on IT support to ensure smooth operations, protect critical data, and drive growth. Yet, ...
Xact IT Solutions
MACI PRONTO

The hidden risks of SaaS for SMBs
Software-as-a-Service (SaaS) tools are revolutionizing the way small and medium-sized businesses (SMBs) operate, offering unparalleled convenience and ...
Xact IT Solutions
MACI PRONTO

5 Tips for selecting the best business server
Whether you’re running a small business or a large enterprise, choosing the right server is a critical decision that impacts your operations and scalability. ...
Xact IT Solutions
MACI PRONTO

Essential criteria for selecting a VoIP headset
In today’s workplace, clear and effective communication is essential, especially for teams using Voice over Internet Protocol (VoIP) systems. Whether ...
Xact IT Solutions
MACI PRONTO

Microsoft 365 Copilot: Flexible purchase options for SMBs
Microsoft 365 Copilot offers a suite of tools powered by artificial intelligence (AI) that can revolutionize the way you work. From automating tasks ...
Xact IT Solutions

Cloud computing trends to watch out for in 2025
Cloud computing has become an indispensable component of modern business operations, thanks to its scalability, flexibility, and cost effectiveness. ...
Xact IT Solutions

3 Game-changing trends for small businesses in 2025
For the millions of small and medium-sized businesses (SMBs) across the world, staying competitive in today’s fast-paced market requires more than ...
Xact IT Solutions

Stay secure in 2025: Cybersecurity resolutions you should keep this year
Cybercrime is more sophisticated and persistent than ever, putting small businesses at significant risk of attack. The new year offers a fresh start, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

U.S. Treasury Breach, Ransomware Attacks, and Lessons for 2025
In the ever-evolving world of cybersecurity, staying informed is not just a luxury—it's a necessity. This week, alarming events have unfolded, demonstrating ...
Xact IT Solutions
XACT IT SOLUTIONS INC
The Cleo Vulnerability: A Wake-Up Call for Cybersecurity in 2025
The end of 2024 brought a stark reminder of the ever-present threat of cyberattacks, with the exploitation of vulnerabilities in Cleo software making ...
Xact IT Solutions

Stay connected anywhere: How iPhone’s satellite texting feature works
In situations where cell towers are out of reach, the iPhone’s satellite texting capability ensures you’re never completely disconnected. Designed ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Rhode Island Faces Ransomware Crisis: What Happened and What It Means for Residents
In a chilling reminder of the growing threat of cybercrime, Rhode Island has become the latest victim of a ransomware attack targeting its state-operated ...
Xact IT Solutions

Things you didn’t know you could do on Windows 11 Task Manager
This article explores the lesser-known features of Windows 11’s Task Manager, offering valuable tips and tricks for optimizing system performance, ...
Xact IT Solutions

Google Cloud vs. Microsoft Azure: A head-to-head comparison
Google Cloud and Microsoft Azure are two dominant forces shaping today’s cloud computing landscape. Both platforms offer a robust suite of services, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Why Every Business Needs a Risk Assessment Strategy Now
Running a business is like driving a high-performance car in a fast-paced race. The thrill of speed, the challenge of competition, and the unrelenting ...
Xact IT Solutions

Balancing joy and wellness: Your guide to staying healthy during the holidays
The holidays bring joy, laughter, and a lot of indulgence. But maintaining balance is key to fully enjoying this special time. Whether you’re trying ...
Xact IT Solutions

Stay secure this holiday season: Strategies for safer online shopping
During the holiday season, skipping the crowds and shopping from your computer or phone is undeniably convenient, but this ease of access comes with ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Get Ready for CMMC Requirements Now
The Cybersecurity Maturity Model Certification (CMMC) is not just another compliance hurdle—it’s a pivotal framework that the U.S. Department of Defense ...
Xact IT Solutions

Optimizing your workspace: Selecting the ideal monitor for enhanced productivity
For remote workers, creating an efficient and ergonomic home office is paramount. While a dedicated workspace is essential, the monitor plays a pivotal ...
Xact IT Solutions

The essential 2025 VoIP systems readiness checklist for your business
Is your Voice over Internet Protocol (VoIP) system ready to meet the demands of 2025? With advancements in communication technologies and the increasing ...
Xact IT Solutions

AI assistants showdown: Copilot Pro vs. Microsoft 365 Copilot
Artificial intelligence (AI) is revolutionizing the modern workplace. With the rise of powerful AI assistants such as Copilot Pro and Microsoft 365 Copilot, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

How to Safeguard Your Business Against Cyberattacks – Insights from a Cybersecurity Expert
In the fast-paced world of today’s digital age, cyber threats are becoming increasingly sophisticated, putting businesses of all sizes at risk. To stay ...
Xact IT Solutions

The benefits of managed IT for businesses this holiday season
The holidays are often the busiest time of year for businesses, so when IT issues arise during this period, they can be particularly disruptive and stressful. ...
Xact IT Solutions

Unwrapping the truth about cyberthreats: A holiday security guide for retailers
The holiday season brings tons of opportunities for retailers to thrive, but it also opens the door to increased cyber risks. With so many people shopping ...
Xact IT Solutions

Safeguard your data with Android’s new features for combating theft
Our smartphones have become an integral part of our lives, containing personal and sensitive information that we can’t afford to lose. Losing your ...
Xact IT Solutions
XACT IT SOLUTIONS INC
Was Starbucks Really Hacked? Not Exactly – Here’s What You Need to Know About the Blue Yonder Cyberattack
Cybersecurity incidents involving major brands often generate headlines, but it’s essential to look closely at the facts. Recently, news reports emerged ...
Xact IT Solutions

Minimize iPhone lag with these simple tricks
It’s a familiar problem: over time, even the fastest phones begin to slow down. Apps take longer to load, screens freeze, and multitasking becomes ...
Xact IT Solutions

VoIP optimization tips for Microsoft Teams
Microsoft Teams is a business essential these days, the tool of choice for seamless communication among organizations of all sizes. However, VoIP calls ...
Xact IT Solutions

A guide to using Windows’ in-place upgrade install
Is your Windows PC running slower than usual or behaving oddly? Before you consider a costly service call, try installing a Windows in-place upgrade. ...
Xact IT Solutions
XACT IT SOLUTIONS INC

What's The Real Cost of CMMC Compliance for DoD Contractors?
In today’s fast-evolving cybersecurity landscape, defense contractors and organizations involved in the Department of Defense (DoD) supply chain face ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Cyberattack on Ohio's Rumpke Waste & Recycling Company: What Went Wrong and How to Protect Your Business
In the ever-evolving world of cybersecurity, we frequently hear about attacks on tech giants, banks, or government agencies. But increasingly, essential ...
Xact IT Solutions

The power of Infrastructure as Code in scaling Internet of Things networks
The Internet of Things (IoT) has been key toward revolutionizing industries, connecting devices, and enabling data-driven insights. However, scaling ...
Xact IT Solutions

Why identity and access management is key to zero trust in healthcare
Protecting sensitive patient data in an era of fast-evolving cyberthreats may render traditional security models obsolete and insufficient. To address ...
Xact IT Solutions

Top holiday cyberthreats retailers need to watch out for
During the holidays, retailers can feel overwhelmed by the number of tasks they need to complete. But while keeping up with the holiday rush, they also ...
Xact IT Solutions
XACT IT SOLUTIONS INC

The Growing Importance of Cybersecurity in Retail: Lessons from Ahold Delhaize’s Recent Cyber Attack
In today’s retail industry, cybersecurity threats are no longer a distant concern—they’re an immediate reality. Recently, Ahold Delhaize, one of ...
Xact IT Solutions

6 Must-have equipment for remote workers
While your office may offer all the necessary tools, creating an efficient home office environment requires thoughtful planning. From ergonomic chairs ...
Xact IT Solutions

VoIP QoS: A quick guide to improve VoIP call quality
If you’re noticing issues such as dropped calls or poor audio quality with your VoIP setup, you’re not alone. While VoIP phone systems offer many ...
Xact IT Solutions

How to create charts and sparklines in Excel
Visualizing data is key to making informed business decisions, and Excel’s chart and sparkline tools make it easy to turn numbers into clear visuals. ...
Xact IT Solutions
Cut costs by following these cloud services tips
Cloud computing offers immense potential for businesses, but without careful management, cloud-related costs can quickly spiral out of control. Learn ...
Xact IT Solutions
Ways automated solutions enhance your marketing efforts
If you want your business to stay competitive, automating key marketing functions is no longer a luxury; it’s a necessity. Automated solutions can ...
Xact IT Solutions

Hack-proof your passwords with the latest NIST password guidelines
Want to outsmart hackers? Start with your passwords. By following the latest guidelines from the National Institute of Standards and Technology (NIST), ...
Xact IT Solutions

Top 7 Android accessories to maximize your smartphone’s potential
Your Android smartphone already does so much, but with the right accessories and peripherals, it can become an even more powerful tool. Discover some ...
Xact IT Solutions

How to wipe your Mac for resale: A brief guide
Selling a used Mac can be a great way to recoup some of its value, especially since Apple products tend to hold up well over time. But before you pass ...
Xact IT Solutions

Effortlessly transfer files between your mobile phone and Windows PC
The process of transferring files from mobile device to PC isn’t the same for everyone, as different devices have different interfaces and compatibilities. ...
Xact IT Solutions

Which is more eco-friendly: A public cloud or a private data center?
As companies evaluate their IT strategies through a sustainability lens, the choice between public clouds and private data centers becomes more nuanced. ...
Xact IT Solutions

How to keep your remote work experience dynamic and engaging
The idea of remote work appeals to many, offering an escape from daily commutes and the promise of flexible scheduling, all while being able to work ...
Xact IT Solutions

The 5 most common security risks to your IT and how to address them
Security breaches often stem from a handful of common threats, both internal and external. Identify the five most IT security risks and learn how to ...
Xact IT Solutions

Boost your home Wi-Fi with these tricks
Slow or unreliable Wi-Fi can be frustrating, especially when working from home. Now more than ever, a stable internet connection is critical. One way ...
Xact IT Solutions

What are the differences between proprietary and open-source VoIP?
VoIP, or Voice over Internet Protocol, has revolutionized communication by allowing businesses to make and receive phone calls over the internet. In ...
Xact IT Solutions

What is an Excel slicer, and how can It help simplify your data?
Spreadsheet software such as Microsoft Excel are incredibly useful, but they can become overwhelming, especially when managing large datasets. Functions ...
Xact IT Solutions

Protect your business from power outages with a quality UPS
Power outages are an unfortunate reality of business life, and their consequences can be severe. From data loss to equipment damage, the impact can be ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Don’t Get Hooked: Understanding and Preventing Phishing Scams
Imagine starting your day with a cup of coffee, ready to tackle your to-do list, when an email that appears to be from a trusted partner lands in your ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Protect Your Business from Within: Defending Against Insider Threats
You might be thinking that you’ve done everything to protect your business from cyberthreats. You have the most advanced security solutions to defend ...
Xact IT Solutions

The hidden dangers of fileless malware
A new generation of malware is on the rise, and it’s proving to be a formidable opponent for businesses of all sizes. Fileless malware is just one ...
Xact IT Solutions
XACT IT SOLUTIONS INC

The Best Ways to Prevent a Cyberattack
Cyberattacks are malicious attempts by hackers to damage, disrupt, or steal data from a system, network, or device. These incidents can lead to massive ...
Xact IT Solutions

How business owners can get the most out of Google Assistant
Managing a small or medium business can feel overwhelming at times, especially when you’re juggling multiple responsibilities. Fortunately, tools such ...
Xact IT Solutions

Simple tips to help extend the life of your iPhone’s battery
Is your iPhone’s battery draining too quickly? You may need to make some configurations to it and adjust your usage habits in order to extend your ...
Xact IT Solutions

Red flags that signal a possible VoIP hack
Voice over Internet Protocol (VoIP) systems are a convenient and cost-effective solution for businesses, but they also present unique security challenges. ...
Xact IT Solutions

Experience the future of work with Windows 365
With the rise of remote and hybrid work, many business leaders and managers face the challenge of ensuring their teams have access to essential tools ...
Xact IT Solutions

Online privacy: Why private browsing matters
In an era where nearly every click, search, and website visit is tracked, maintaining true anonymity online has become increasingly difficult. Whether ...
Xact IT Solutions

Key factors for choosing the ideal EMR system
Modern healthcare documentation requires both accuracy and efficiency, which is why electronic medical records (EMRs) have become essential for managing ...
Xact IT Solutions

How cybercriminals bypass MFA and what you can do about it
Do you feel more secure knowing that you have multifactor authentication (MFA) in place? While MFA is a powerful security measure, it’s important to ...
Xact IT Solutions

HDDs vs. SSDs: The differences between two storage solutions
When it comes to data storage, two main types of drives dominate the market: hard disk drives (HDDs) and solid-state drives (SSDs). While HDDs, which ...
Xact IT Solutions

Microsoft Office not working? Try these fixes
Is Microsoft Office giving you trouble? Don’t worry; fixing it isn’t as difficult as you think. Our user-friendly guide will help you identify and ...
Xact IT Solutions

Don’t lose your audience in seconds: Tips for creating engaging websites
In the age of instant gratification, a website that takes too long to load or is difficult to navigate can quickly lose visitors. To keep your audience ...
Xact IT Solutions

The strategic advantages of adopting virtual reality
Virtual reality (VR) allows users to experience and interact with digital environments. While it has been primarily associated with entertainment, VR ...
Xact IT Solutions

A quick guide to VPNs: The benefits and the criteria for choosing a trustworthy VPN
Even with firewalls and anti-malware software in place, cybercriminals can still intercept your data if you don’t take extra precautions, such as using ...
Xact IT Solutions

How to shield your Android devices from ransomware
With the rise of mobile technology, cybercriminals have turned their attention to Android devices, creating ransomware that can lock users out of their ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Understanding the Latest Cyber Threat: A Deep Dive into the US Marshal Service Hack
Recently, reports have surfaced that Hunters International has leaked an enormous 386 gigabytes of sensitive data from the US Marshal Service. As of now, ...
Xact IT Solutions

Got a new Apple MacBook? Here’s how you can set it up properly
Tailor your MacBook experience to your unique preferences with our simple setup guide, where we’ll cover the basics, such as creating your Apple ID ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Cyberattack Grounds Seattle Airport: A Wake-Up Call for Cybersecurity
A recent cyberattack on Seattle-Tacoma International Airport has disrupted operations, causing significant flight delays and cancellations.
This incident ...
Xact IT Solutions

The complete guide to business phones in 2024
In 2024, choosing the right phone system is more important than ever to stay ahead of the competition. This comprehensive guide will walk you through ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Weekly Cybersecurity Roundup: Major Ransomware Attacks You Need to Know About
This week, there have been several notable cyberattacks, and while I usually focus on just one major incident, I’m changing things up. Moving forward, ...
Xact IT Solutions

How to remove bloatware in Windows 11
Tired of your Windows 11 laptop or desktop running slower than it should? It might be time to tackle the bloatware that’s slowing it down. In this ...
Xact IT Solutions

How AI will transform your web browsing experience
Artificial intelligence (AI) has done many amazing things. It has revolutionized the way we interact with technology, making our lives easier and more ...
Xact IT Solutions

HIPAA and social media: Violations, consequences, and tips
Social media can help healthcare organizations advertise services, engage with patients, and foster a sense of community. However, one slip, and you ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Social Security Breach 2024: Protect Yourself from the Largest Data Leak in U.S. History
Today, we're diving into a topic that's taken the internet by storm—something that has almost every American worried—the massive data breach that ...
Xact IT Solutions

Tips on choosing a projector for your business
Projectors are essential tools for delivering impactful presentations. However, selecting the optimal projector for your business can be challenging ...
Xact IT Solutions

Boost your business with these VoIP services
As traditional phone systems become obsolete, businesses are turning to more innovative communications solutions. Voice over Internet Protocol (VoIP) ...
Xact IT Solutions
How to share your Outlook calendar like a pro
Outlook makes it easy to share your calendar with others. Whether you want to share your availability with colleagues, coordinate family events, or plan ...
Xact IT Solutions
XACT IT SOLUTIONS INC

The Alarming State of Ransomware in 2024: Costs, Trends, and How to Protect Your Business
In 2024, ransomware has continued to be one of the most devastating cyber threats facing businesses globally. As we explore this escalating crisis, it ...
Xact IT Solutions

Leveraging AI to drive eCommerce business growth
Artificial intelligence (AI) provides plenty of opportunities for eCommerce businesses looking to improve their online sales. By leveraging AI, businesses ...
Xact IT Solutions
XACT IT SOLUTIONS INC

McLaren Health Faces IT Disruption Amid Cyberattack Concerns
In a troubling repeat of last year's events, McLaren Health Care in Michigan is once again grappling with a significant IT disruption, raising ...
Xact IT Solutions

Picking the MSP for you: The basics and what to consider
Small and medium-sized businesses often stretch themselves thin, with IT management becoming a significant burden. Seeking external IT support through ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Everything You Need to Know About Cybersecurity
Cybersecurity involves practices and technologies to protect computers, networks, programs, and data from unauthorized access and attacks. Essentially, ...
Xact IT Solutions
Steps to protect your business from cyberattacks
Many small-business owners believe their companies are immune to cyberattacks, thinking cybercriminals target only larger organizations. However, small ...
Xact IT Solutions

Effective measures to protect your Mac against ransomware
Macs may be known for their security, but they’re not immune to ransomware attacks. And with cybercriminals constantly evolving their tactics, it’s ...
Xact IT Solutions
XACT IT SOLUTIONS INC

The Recent Hack of Leidos Holdings: A Wake-Up Call for Cybersecurity
Recently, Leidos Holdings, a major IT service provider to the Pentagon and other prominent US government agencies, faced a significant hack. This event ...
Xact IT Solutions

Windows not booting? Follow these tips to get your PC up and running
Facing a Windows startup problem can be alarming, but there’s no need to panic. This blog provides step-by-step solutions to common boot issues, guiding ...
Xact IT Solutions

Navigating a successful UC cloud migration: 5 Crucial steps
Transitioning your unified communications (UC) system to the cloud is a strategic move that can significantly enhance business operations. However, this ...
Xact IT Solutions
XACT IT SOLUTIONS INC
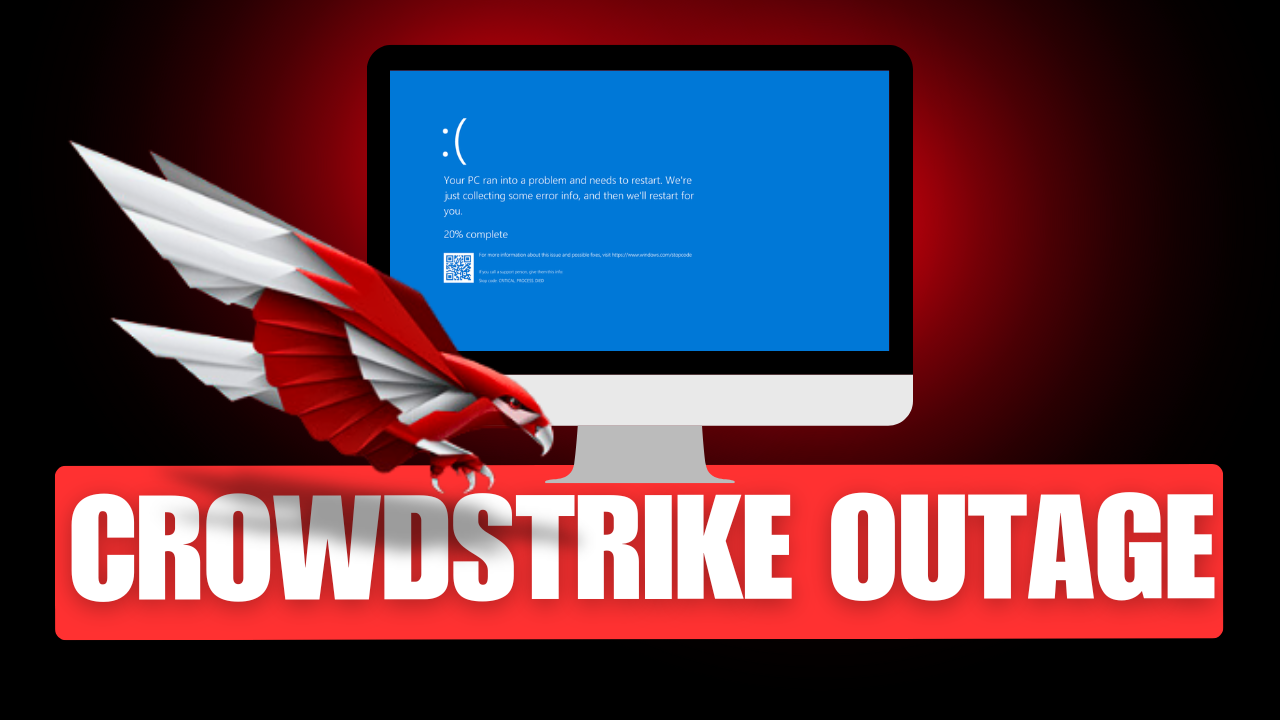
CrowdStrike and Microsoft Outage: A Global IT Disruption
This blog provides the latest update on the CrowdStrike-Microsoft outage, which has caused a global IT disruption affecting thousands of companies worldwide. ...
Xact IT Solutions
XACT IT SOLUTIONS INC
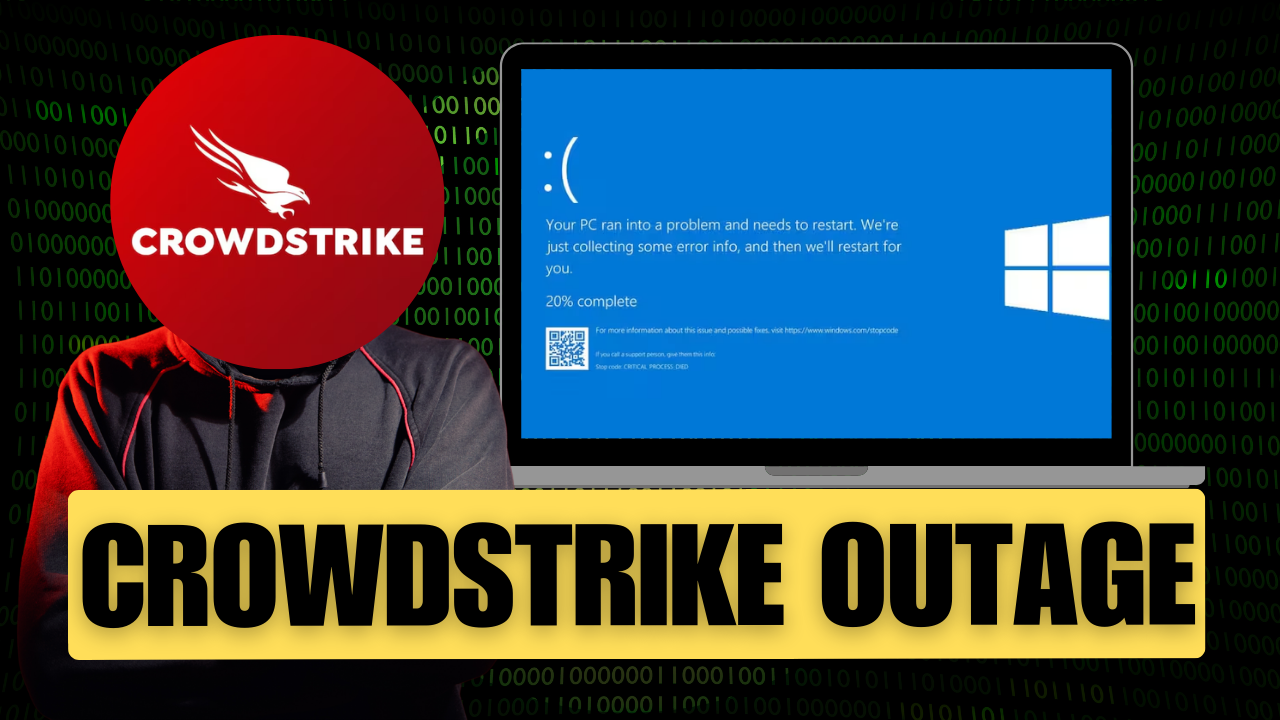
Microsoft / CrowdStrike Outage Causes Global Disruptions: Airports, Banks, and More Affected
So, what’s going on with CrowdStrike? From what I've gathered, CrowdStrike rolled out an update that conflicted with Windows, causing many systems to ...
Xact IT Solutions

3 Security advantages of the cloud
Small and medium-sized businesses (SMBs) no longer need to view cybersecurity as an insurmountable challenge. Cloud technology has transformed the security ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Rite Aid Data Breach: What You Need to Know
It was recently announced that approximately 2 million Rite Aid customers had their information stolen. This breach occurred several years ago, before ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Massive Cyberattacks on AT&T and Disney: What You Need to Know
AT&T recently disclosed a massive data breach in which hackers stole phone call records and text message metadata from nearly all their customers. ...
Xact IT Solutions

Tips for protecting your business’s corporate data
Recent cyberattacks on multinational corporations highlight the ever-present risk of data breaches. For businesses of all sizes, a data breach can be ...
Xact IT Solutions

Boost your browsing: Fixing slow mobile internet in 5 easy steps
Is your mobile internet dragging its feet? A sluggish connection can be a major inconvenience in today’s fast-paced world, disrupting work, streaming, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Patelco Credit Union's Ransomware Crisis: A Deep Dive into the Aftermath and Response
Patelco Credit Union recently found itself at the center of a major ransomware attack. This incident has resulted in lawsuits and significant financial ...
Xact IT Solutions

Key considerations in selecting the ideal small-business VoIP system
Effective communication is vital for any business’s success, and Voice over Internet Protocol (VoIP) systems are transforming how companies handle ...
Xact IT Solutions

Top tips for a safe and secure Microsoft Teams experience
Microsoft Teams is a popular business collaboration platform that has also drawn the unwanted attention of cybercriminals. If these malicious actors ...
Xact IT Solutions
XACT IT SOLUTIONS INC

CDK Global Cyberattack: Impact to the Auto Industry and Economy
The automotive industry is facing a significant upheaval due to a recent cyberattack on CDK Global, a prominent provider of IT and digital marketing solutions ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Crown Equipment's Cyberattack: Recovery and Lessons Learned
Several weeks ago, Crown Equipment faced a serious cyberattack that disrupted its operations. Employees quickly took to the internet to express their ...
Xact IT Solutions

Essential steps for hurricane disaster recovery
Imagine this: a hurricane is on the horizon, and you’re scrambling to protect your business. Don’t get caught off guard! Here’s a straightforward ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Patelco Credit Union Ransomware Attack: What You Need to Know
Over the weekend, Patelco Credit Union fell victim to a ransomware attack, leading to a complete shutdown of their online banking services, mobile apps, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Need More Reliable IT Services for Your Business?
Today's businesses depend heavily on technology for success and growth. However, navigating complex tech issues and ensuring all your systems stay up-to-date ...
Xact IT Solutions
XACT IT SOLUTIONS INC

From Tech Headaches to Seamless Operations: The Impact of a Strategic IT Service Provider
Technology is critical in driving business success in today’s fast-paced digital landscape. However, managing IT infrastructure and systems can be a ...
Xact IT Solutions

Mitigate risk and proactively secure your business with these tips
The evolving threat landscape poses a significant financial risk to businesses. Cyberattacks can lead to costly data breaches, operational disruptions, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

TeamViewer Breach by APT29 - What You Need to Know
TeamViewer has confirmed a breach of their internal network by the notorious Russian state-sponsored hacking group APT29, also known as Cozy Bear or Midnight ...
Xact IT Solutions

Rev up your Mac: 5 Essential tips for speed optimization
Is your Mac feeling sluggish? Are applications taking forever to load? Don’t despair. As we fill our computers with apps, files, and updates, even ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Federal Reserve Hack Update: LockBit delivers - did they actually hack The Fed?
In recent cybersecurity news, the notorious LockBit 3.0 ransomware group has made headlines by claiming to have breached the Federal Reserve. Over the ...
Xact IT Solutions

Navigating the new age of business phone systems
In the past, business phone systems were synonymous with bulky hardware, complicated wiring, and limited features. These traditional systems anchored ...
Xact IT Solutions

Transform website traffic into website conversions with 5 key strategies
Traffic alone doesn’t guarantee website success. Even with a high volume of visitors, conversions might be low, meaning those visitors aren’t subscribing, ...
Xact IT Solutions

Safeguarding your privacy: Webcam protection tips for Windows users
Webcams are a staple feature in modern computing devices, allowing users to connect with others through video calls, conferences and live streaming. ...
Xact IT Solutions
XACT IT SOLUTIONS INC

How Long Are Companies Down After a Cyberattack? Understanding Ransomware Recovery
In today's digital age, the threat of cyber attacks looms large over businesses worldwide. The recent ransomware incidents involving Crown Equipment and ...
Xact IT Solutions
XACT IT SOLUTIONS INC
CDK Global Cyberattack: What This Means for the Automotive Industry
In a significant development affecting the automotive industry, CDK Global, a leading provider of integrated technology solutions for automotive retail, ...
Xact IT Solutions

Simple exercises to keep you fit while working from home
When people work from home, their daily physical activity often decreases. Unlike commuting to work and walking around the office, home-based work tends ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Crown Equipment Cyberattack: A Closer Look
Crown Equipment, a global leader in forklift manufacturing, is reeling from a major cyberattack. What started as murmurs of potential disruptions quickly ...
Xact IT Solutions

How to choose the right mouse: A comprehensive buyer’s guide
One essential tool that often gets overshadowed, but has a surprisingly big impact on your daily tech interactions, is your trusty mouse. Whether you’re ...
Xact IT Solutions
Mastering your presentation skills: A guide to using PowerPoint Presenter Coach
Giving a PowerPoint presentation doesn’t have to be a daunting task with the right tools. PowerPoint Presenter Coach is one such tool that’s designed ...
Xact IT Solutions

The VoIP revolution: Future-proofing business communications
The world of business communication is rapidly transforming, and staying ahead requires embracing technologies that can grow with you. Voice over Internet ...
Xact IT Solutions
XACT IT SOLUTIONS INC

The Rising Tide of Cyber Attacks on US Cities – Cleveland's Latest Ordeal
https://www.youtube.com/watch?v=e3TzUQ3iSAs
Another major US city has fallen victim to a crippling cyber attack. Following the recent breach ...
Xact IT Solutions
XACT IT SOLUTIONS INC
The Rising Threat of Ransomware and What It Means for Businesses
https://www.youtube.com/watch?v=Np116UYXQqA&t=94s
If you thought ransomware was on the decline, think again. The past few weeks have been a whirlwind ...
Xact IT Solutions

Helpful Google Chrome extensions to boost your productivity
Productivity is a major issue in the workplace due to such things as information overload and time-consuming tasks. Fortunately, there are easily available ...
Xact IT Solutions

Common IT investment mistakes to avoid
Investing in new technology is a powerful way to drive business growth. Whether you’re purchasing new servers to boost productivity or subscribing ...
Xact IT Solutions

Key practices to strengthen your email security posture
Email remains a cornerstone of modern business communication, valued for its speed, ease of use, and convenience. However, it also presents a potential ...
Xact IT Solutions

How to stretch your data plan: Top tips for Android users
For Android users, staying within mobile data limits can be a challenge, especially with the increasing number of apps and services vying for bandwidth. ...
Xact IT Solutions
XACT IT SOLUTIONS INC

The Ascension Healthcare Ransomware Attack: A Deep Dive into the Impact and Implications
https://www.youtube.com/watch?v=e46YulxJjLM&t=1s
In the rapidly evolving landscape of cybersecurity threats, healthcare organizations have emerged ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Debunking Myths About AI in Cybersecurity
AI has become a buzzword that often evokes a mix of awe, doubt, and even fear, especially in cybersecurity. However, the fact is that if used effectively ...
Xact IT Solutions
XACT IT SOLUTIONS INC

How Cybercriminals Use AI to Power Their Attacks
Managing a business on your own is challenging enough without worrying about cyberattacks. However, there is cause for alarm as hackers are using artificial ...
Xact IT Solutions

Unlocking the full potential of remote work with VoIP
As businesses adapt to the evolving landscape of remote work, the need for robust and efficient communication tools becomes increasingly critical. Voice ...
Xact IT Solutions

Ad-free experience: Step-by-step instructions to disable ads in Windows 11
Windows 11 brings a host of new features and a fresh interface, but it also comes with an unwelcome addition: ads. Whether they’re in the Start Menu, ...
Xact IT Solutions

4 Gmail strategies to improve email efficiency
Feeling perpetually behind on emails? The constant deluge in today’s digital world can cripple even the most focused professional. While Gmail excels ...
Xact IT Solutions
XACT IT SOLUTIONS INC
The Growing Cybersecurity Threat to Family Offices: What You Need to Know
https://www.youtube.com/watch?v=nvO7of79YG0
In today’s rapidly evolving digital landscape, cybersecurity has become a crucial concern for businesses ...
Xact IT Solutions

Unlocking the power of cloud computing in healthcare
Delivering high-quality patient care is a primary goal for any healthcare practice. Cloud computing supports this goal by offering reliability, convenience, ...
Xact IT Solutions

Building a collaborative cybersecurity culture with Gen Z employees
Gen Z’s digital fluency presents a valuable opportunity to strengthen your company’s cybersecurity posture. This blog post will explore strategies ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Cybersecurity Roundup: A Week of DDoS Attacks, Dark Web Takedowns, and Rising Ransomware Threats
The ever-changing cybersecurity landscape keeps us all on our toes. This week has been no different, with developments highlighting both the growing sophistication ...
Xact IT Solutions
8 Tips to save energy on your PC
Conserving energy while using your PC daily can be quite challenging. A typical desktop setup, including loudspeakers and a printer, can consume nearly ...
Xact IT Solutions

Turn hold time into gold by enhancing your VoIP on-hold messages
For many businesses, Voice over Internet Protocol (VoIP) on-hold messages are an afterthought — a necessary evil to fill the silence while customers ...
Xact IT Solutions
XACT IT SOLUTIONS INC
The Wichita Ransomware Crisis: A Wake-Up Call for Municipal Cybersecurity
Wichita, Kansas recently found itself thrust into the spotlight for reasons no city ever wishes for – a crippling ransomware attack.
As the dust ...
Xact IT Solutions

Combat phishing with Microsoft 365 Defender
Phishing might sound complicated, but the basic concept is simple: deception. Criminals try to trick you into revealing personal information or clicking ...
Xact IT Solutions

The advantages of private browsers for protecting your online privacy
As the internet evolves, so do the risks associated with online activities. Private browsers are an often overlooked tool for protecting your online ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Law Enforcement Identifies LockBit Ransomware Admin: What It Means for Cybersecurity
Ransomware groups have long been inflicting significant damage on companies, government entities, and individuals. Recently, ...
Xact IT Solutions
XACT IT SOLUTIONS INC
Ascension Healthcare Ransomware Attack: A Look at Cybersecurity Vulnerabilities
Ascension, one of the largest healthcare systems in the United States, has been thrown into chaos by a ransomware attack. This cyberattack, discovered ...
Xact IT Solutions

How cloud-based OMS empowers your eCommerce business
eCommerce thrives on happy customers, but managing a growing order volume can strain your ability to deliver exceptional experiences. What’s worse, ...
Xact IT Solutions
XACT IT SOLUTIONS INC
How to Choose the Right SaaS Backup Solution for Your Business
As technology continues to advance, more and more businesses like yours are adopting Software-as-a-Service (SaaS) applications due to their flexibility, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

The Most Dangerous Myths About Cloud Data Backup
For businesses, Software-as-a-Service (SaaS) solutions offer unparalleled opportunities to enhance efficiency, scalability and overall operations. However, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Panda Restaurant Group Data Breach and More: A Cybersecurity Rundown
Our digital world can be a double-edged sword. Convenience often comes at the cost of vulnerability, and recent cyber events remind us of this harsh reality.
Dining ...
Xact IT Solutions

Hackers 101: Understanding the different types and what they do
Back in the 1950s, the term “hacker” simply described someone who enjoyed tinkering with computers and pushing their boundaries. However, with the ...
Xact IT Solutions

Enhance your Android user experience by syncing with Google Chrome
By leveraging Google Chrome’s data synchronization with Android devices, users achieve a streamlined workflow. This cross-device compatibility fosters ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Are We Prepared for a Chinese Cyberattack on Critical Infrastructure?
https://www.youtube.com/watch?v=HnBH4iiGjmg&t=433s
The FBI Director's recent warnings paint a chilling picture: Chinese state-sponsored hackers are ...
Xact IT Solutions

Why softphones are the perfect business communication solution
Are you searching for a communication solution that’s as dynamic as your business environment? Softphones emerge as a compelling contender, offering ...
Xact IT Solutions

7 Windows features that drive you nuts (and how to fix them)
If you’re one of the millions navigating the digital world through a Windows device, you’ve probably stumbled over some hidden tripwires that can ...
Xact IT Solutions

Image optimization strategies: Boosting SEO for your website
Website images are crucial for engaging visitors, conveying brand messaging, and showcasing products or services. Their impact on search engine optimization ...
Xact IT Solutions

How blockchain is changing healthcare
Beyond its original use in securing cryptocurrency, blockchain technology is making waves across various industries, with healthcare being a prime example. ...
Xact IT Solutions

Simple steps to protect your online presence
With cyberthreats on the rise, businesses must prioritize online security to safeguard sensitive information and maintain customer trust. The good news ...
Xact IT Solutions
XACT IT SOLUTIONS INC

New York DFS Cybersecurity Regulations: A Guide for Businesses
In today's digital landscape, cybersecurity is paramount for businesses of all sizes. This article explores the New York Department of Financial Services ...
Xact IT Solutions

BYOD vs. CYOD: Selecting the right mobile device management strategy for your business
In today’s mobile-first environment, organizations have a critical decision to make regarding employee device usage. Two prominent strategies exist: ...
Xact IT Solutions

5 Security measures you need for VoIP
Businesses are increasingly relying on Voice over Internet Protocol (VoIP) systems due to their cost-effectiveness and enhanced features. However, VoIP ...
Xact IT Solutions

Unlock your team’s peak productivity with Viva Insights
Wondering how your team can get past its productivity plateau? Feeling like there’s untapped potential hidden within your workflows? Your search for ...
Xact IT Solutions

Ditch the password! Unlock the power of mobile biometrics
In an age where we carry our lives in our pockets, mobile security is paramount. The standard of typing in a password to unlock or authenticate your ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Insights into the Omni Hotels IT Outage: A Closer Look
In the hospitality industry, reliability and seamless operations are paramount. Yet, recently, Omni Hotels, one of the largest hotel chains in the United ...
Xact IT Solutions

6 Common disaster recovery myths every business should know
Cyberattacks, system failures, and natural disasters have become a common occurrence, and they’re becoming increasingly more disruptive as businesses ...
Xact IT Solutions

Understanding the role of cyber insurance
The evolving cyberthreat landscape poses a significant risk to small businesses. Cybercriminals often target such businesses due to the valuable data ...
Xact IT Solutions
XACT IT SOLUTIONS INC
Top 5 Threats IoT Devices Pose to Data Protection & Privacy
How secure is your IoT (Internet of Things) data? If you don’t know the answer, you could be in trouble.
Yes, IoT devices, or “smart” gadgets, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

How to Beef Up Your Incident Response Plan
Are you prepared to face a cybersecurity breach, a natural disaster or a system failure?
Such disruptive events can strike at any moment, causing chaos ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Don’t Make These Incident Response Planning Mistakes
Are you worried about cyberattacks hitting your business? You're not alone.
Cyberattacks pose a real danger to businesses like yours and without a ...
Xact IT Solutions

How to maximize your MacBook’s battery life and life span
In today’s fast-paced business world, a reliable battery is a must-have for staying connected and productive. Whether you’re in the office or on ...
Xact IT Solutions

Tips for enhancing your productivity with an Android tablet
The rise of mobile workforces has led to a surge in the adoption of Android tablets. However, managing these devices across a distributed team can present ...
Xact IT Solutions
ALLEN PAJAR

Unified communications: Top advantages for SMBs
If you want to streamline your company’s operations, unified communications (UC) might be the solution you’re searching for. UC offers numerous benefits ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Protecting US Water Systems from Cyber Attacks: An Urgent Need
The recent warning issued by the Biden administration to governors across all 50 states regarding the vulnerability of water and wastewater facilities ...
Xact IT Solutions

Organize your digital space: Top techniques for a tidy desktop
Does staring at a cluttered desktop filled with icons make you groan? You’re not alone. A messy digital space can zap your productivity and make finding ...
Xact IT Solutions
ALLEN PAJAR

2024 design trends that will elevate your small business’s website
Your website is a powerful tool to showcase your brand story. 2024 emphasizes the use of narrative-driven layouts, interactive features, and personalized ...
Xact IT Solutions

Defending healthcare data: How to keep PHI safe from cyberattacks
Safeguarding protected health information (PHI) is vital for healthcare institutions worldwide. PHI, which encompasses a broad spectrum of data from ...
Xact IT Solutions
XACT IT SOLUTIONS INC

CISA Hacked: Foreign Adversaries May be Responsible
In the past week, the United States Cybersecurity and Infrastructure Security Agency (CISA), has fallen victim into a cyberattack.
First things first, ...
Xact IT Solutions

Applying NIST guidelines to improve password security
When it comes to password generation and security, many people tend toward bad practices, such as passwords based on their birthday or using the same ...
Xact IT Solutions
XACT IT SOLUTIONS INC
The Rising Threat of Ransomware: Insights from FBI's Internet Crime Report
In recent years, the scourge of ransomware has reached unprecedented levels, posing significant threats to individuals and businesses alike. The latest ...
Xact IT Solutions
ALLEN PAJAR

Essential laptop features for work from anywhere
Remote work allows you to work from anywhere, from kitchens to coworking spaces. But to truly thrive in this flexible environment, you need a laptop that ...
Xact IT Solutions

Leveraging AI to revolutionize business communications
Having implemented Voice over Internet Protocol (VoIP) for increased efficiency and cost savings, the next step for many businesses is to explore the ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Ward Trucking Cyberattack: A Closer Look
Imagine ordering something online, and eagerly awaiting its delivery, only to find out that the entire system supporting the delivery process has been ...
Xact IT Solutions

How your smartphone’s biometrics boosts your online protection
Your smartphone is no longer just a communication device; it’s a portal to your entire digital life, from banking apps to social media accounts. While ...
Xact IT Solutions

Work smarter, not harder: Practical tips for increased staff efficiency
Feeling like there just aren’t enough hours in the day? This guide provides practical tips and strategies you can implement to empower your team to ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Black Cat Ransomware: Why they Attacked Change Health
The Black Cat Ransomware group has emerged as a significant threat, particularly in the healthcare sector. This criminal organization, known for orchestrating ...
Xact IT Solutions

How hackers can infiltrate your systems
While technology empowers us in many ways, it also opens up vulnerabilities that can be exploited by malicious actors. When breaching your systems, hackers ...
Xact IT Solutions

Android adware removal and protection tips: A quick guide
The vast library of applications on the Google Play Store provides countless options, but too many of these apps contain undesirable software such as ...
Xact IT Solutions
XACT IT SOLUTIONS INC
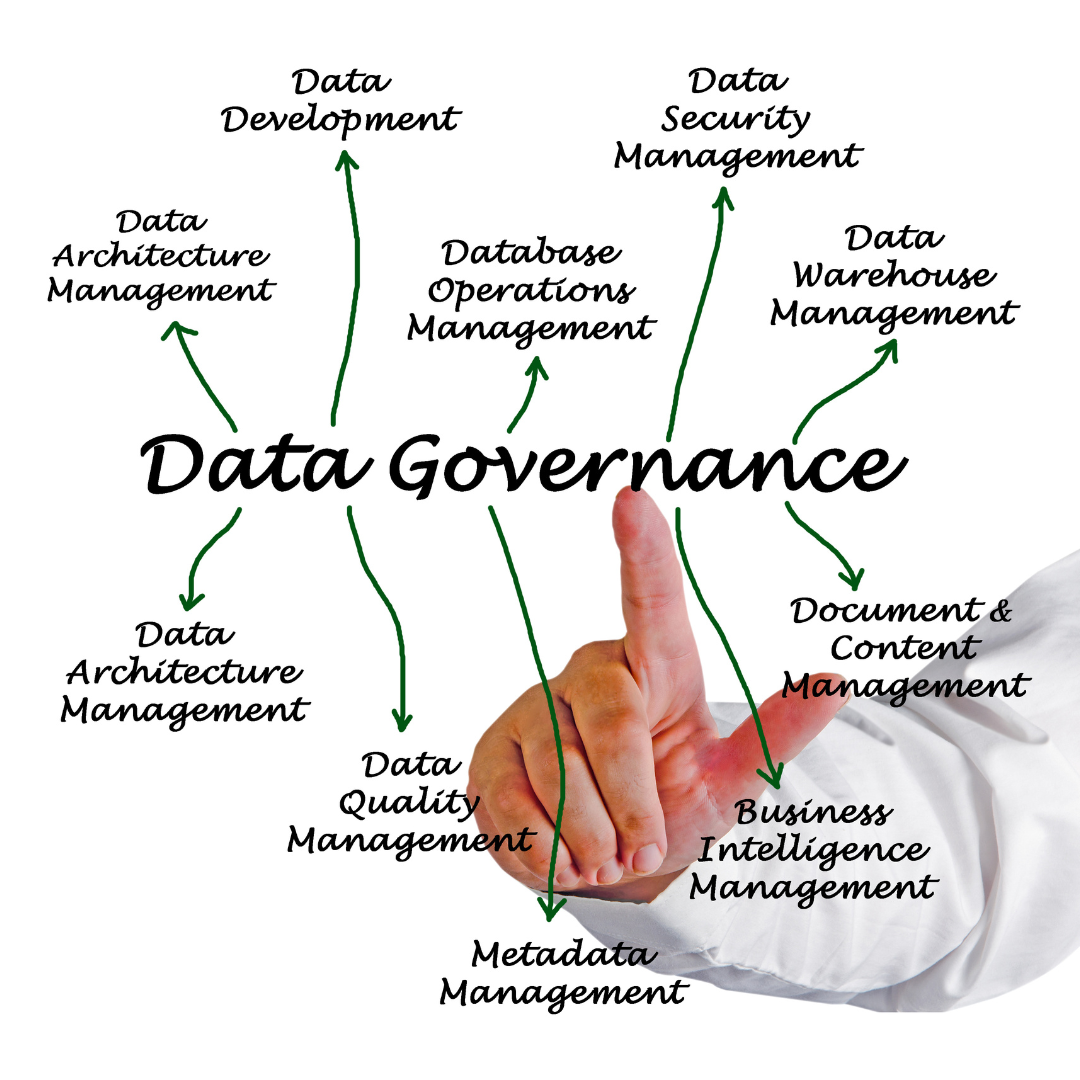
A Deep Dive Into Data Governance
In the world of business, your data holds the key to understanding customers, market trends, and internal operations. Making the most of this information ...
Xact IT Solutions
XACT IT SOLUTIONS INC

The Hidden Costs of Ineffective Data Management
In today's business landscape, data isn't just power -- it's the very lifeline that fuels business decisions, drives innovations, and shapes strategies. ...
Xact IT Solutions

Understanding the costs of owning a VoIP system
If you’re looking to upgrade your communication solution without burning a hole in your pocket, switching to Voice over Internet Protocol (VoIP) systems ...
Xact IT Solutions

Enhance your productivity with Microsoft Edge’s innovative features
In today’s fast-paced digital landscape, choosing the right browser isn’t just about convenience; it’s about efficiency, security, and maximizing ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Millions Impacted by Staggering Series of Cyberattacks
This blog reveals some of the most recent cyberattacks, breaches, and ransomware incidents that have recently shaken organizations worldwide. If you are ...
Xact IT Solutions

What you need to know about virtualization and cloud computing
Two terms often thrown around the digital landscape are virtualization and cloud computing. While they are similar technologies, they have distinct differences. ...
Xact IT Solutions

The verdict on EHRs: Is the shift from paper records in healthcare worth it?
In recent years, there has been a significant push toward digitizing healthcare records. The traditional method of using paper charts and files to store ...
Xact IT Solutions

Is it worth monitoring employees online?
The digitization of the workplace has opened up new frontiers for employer oversight. With workers more connected than ever through computers and internet-based ...
Xact IT Solutions
XACT IT SOLUTIONS INC

True love or fraud? Here’s how you’ll know.
In search of true love this Valentine’s Day, some people may just find themselves becoming the victim of a scam. Recent data shows that at least 18,000 ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Understanding the Dark Web
For most people, using the internet means opening a Google browser, or scrolling through social media apps like Facebook, YouTube, or Instagram. However, ...
Xact IT Solutions

Troubleshoot your printer: The 4 most common problems and solutions
1. Paper jams
The paper jam is the most common and recurring of printer problems. It arises from various mechanical issues, including overfilled paper ...
Xact IT Solutions

VoIP softphones vs. hardphones: Guide to VoIP phone systems
Voice over Internet Protocol (VoIP) is among the most important tools for remote or hybrid work. Nowadays, companies can choose between VoIP softphones ...
Xact IT Solutions

Optimize your Microsoft 365 apps investment with Admin Center
Ensuring optimal user experience and robust cybersecurity demands a skilled IT administrator. Their responsibilities encompass workflow supervision, ...
Xact IT Solutions

5 Web conversion tips you should implement ASAP
When it comes to having an online presence, maximizing conversions is a major goal. This means ensuring that a company’s website seamlessly transforms ...
Xact IT Solutions

5 Proven techniques to boost your team’s efficiency
Keeping pace with today’s business landscape demands a hyper-efficient team. Optimizing team productivity isn’t therefore just nice to have: it’s ...
Xact IT Solutions

Navigating the cybersecurity landscape: Must-have training for a secure digital future
In today’s digital landscape, cybersecurity is an indispensable aspect of running a small business. With the increasing prevalence of online threats, ...
Xact IT Solutions

A Mac user’s guide to malware warfare
The myth of Macs being invincible to malware has long been shattered. But there are those who still believe this myth, and so may find themselves facing ...
Xact IT Solutions
XACT IT SOLUTIONS INC

A.I. Wants To Help Us Shop – Are We Okay With That?
Log in to Amazon, and you’ll see suggested products like winter decorations, novels, or toy recommendations for kids. Add that remote-controlled car ...
Xact IT Solutions
XACT IT SOLUTIONS INC

A “Culture Of Appreciation” Improves Work And Customer Loyalty: Here’s How To Make Your Own
The desire to feel valued, recognized, and appreciated is universal in Western culture, not only in our personal lives but also in the workplace. According ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Show Some Love To Your Business Continuity Plan
Wintertime can feel like a wonderland. There’s hot cocoa, cozy fireside conversations, glistening white snowfall…ice storms, power outages, and tons ...
Xact IT Solutions

Boost your efficiency in 2024 with these Android productivity apps
Today, Android users have countless apps to choose from to help them stay organized, focused, and efficient. But with so many options available, it can ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Best Practices To ‘Celebrate’ National Change Your Password Day: How Does Your Password Stack Up?
Each year on February 1st, we celebrate Change Your Password Day. While it’s not a holiday that gets you off work, it serves as a good opportunity each ...
Xact IT Solutions

Safeguard your business VoIP against TDoS: A quick guide
Voice over Internet Protocol (VoIP) provides organizations with many advantages, including improved call quality, better scalability and mobility, and ...
Xact IT Solutions
XACT IT SOLUTIONS INC

How “Cheaper” IT Providers Sneak In Expensive Hidden Costs
Is your company looking to hire an IT firm? Unfortunately, unless you’re tech-savvy or experienced with IT contracts, there can be hidden costs that ...
Xact IT Solutions
XACT IT SOLUTIONS INC

New Security Features To Protect Your Phone In 2024
Long gone are the days when phones were simple devices used to make calls. Today our phones are advanced, handheld supercomputers that can do everything ...
Xact IT Solutions
XACT IT SOLUTIONS INC

5 New Cybersecurity Threats You Need To Prepare For This 2024
The year 2023 marked a significant turning point for cyber-attacks with the introduction and wide proliferation of AI (artificial intelligence), now in ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Beware Of Cybersquatters!
Have you ever searched for a specific website but landed on a completely different one after misspelling a letter or two in the URL? This deceptive tactic ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Your 15-Step IT Profitability Road Map For 2024
If you’re hoping to cut costs and boost profitability in 2024 without compromising productivity or efficiency, assessing the technology you use in day-to-day ...
Xact IT Solutions
XACT IT SOLUTIONS INC

How IT Support Companies Charge For Their Services – Part 2 Of 2
Continuing from our previous blog post, we’re answering one of the most common questions we get from new prospective clients: “What do you charge ...
Xact IT Solutions
XACT IT SOLUTIONS INC

How IT Support Companies Charge For Their Services – Part 1 Of 2
Before you can accurately compare the fees, services, and deliverables of one IT services company to that of another, you need to understand the two predominant ...
Xact IT Solutions
Windows 11 made easy: 6 Features to boost your laptop’s security and performance
Microsoft’s latest operating system, Windows 11, brings numerous improvements compared to its predecessors. To get the most out of these improvements ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Bolster Cyber Defenses With Routine Security Tests
Businesses today face a range of cybersecurity threats, from social engineering attacks like phishing to sophisticated ransomware. For business leaders ...
Xact IT Solutions
XACT IT SOLUTIONS INC

The Hidden Challenges of Network Monitoring
Your network is your business’s lifeline.
A healthy and secure network is critical for seamless communication and operational efficiency. That’s ...
Xact IT Solutions

A strategic guide to web hosting solutions
In today’s digitally driven landscape, a robust online presence is no longer a luxury, but a critical business imperative. Regardless of your industry ...
Xact IT Solutions

Data-driven interventions: Preventing readmissions before they happen
The traditional reactive approach to healthcare — treating patients after they fall ill — is undergoing a profound shift. Today, because of big data, ...
Xact IT Solutions

A guide to watering hole attacks: Recognizing the danger and bolstering your digital armor
Watering hole attacks are one of the most common types of cyberattacks that can pose a significant threat to both individuals and organizations. In this ...
Xact IT Solutions

5 Effective strategies for keeping servers and computer hardware cool
Today, servers and computer hardware are constantly being pushed to their limits. And with increased performance comes the challenge of keeping these ...
Xact IT Solutions

Top 6 VoIP trends for 2024
VoIP has delivered incredible changes, not just to the telecommunications industry but to the business landscape in general. By combining flexible features ...
Xact IT Solutions

How to boost your productivity with Microsoft Word
Microsoft Word is a powerful tool that millions of people use every day, but many are not aware of its features that can significantly enhance productivity. ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Fidelity National & Mr. Cooper Mortgage Cyberattacks: Unveiling the Aftermath
Fidelity National Financial and Mr. Cooper, both prominent players in the real estate industry, found themselves grappling with severe cybersecurity breaches ...
Xact IT Solutions

7 Cloud strategies for 2024 to help you innovate, optimize, and protect
Ditch the rigid IT infrastructure — 2024 is all about flexibility and cost-efficiency. Serverless computing lets you focus on your core business without ...
Xact IT Solutions

2024 technology trends: What you need to know
The world of IT is abuzz with new technologies that promise a new way of life. From quantum computers to solar electric vehicles to robot-assisted surgery, ...
Xact IT Solutions
XACT IT SOLUTIONS INC
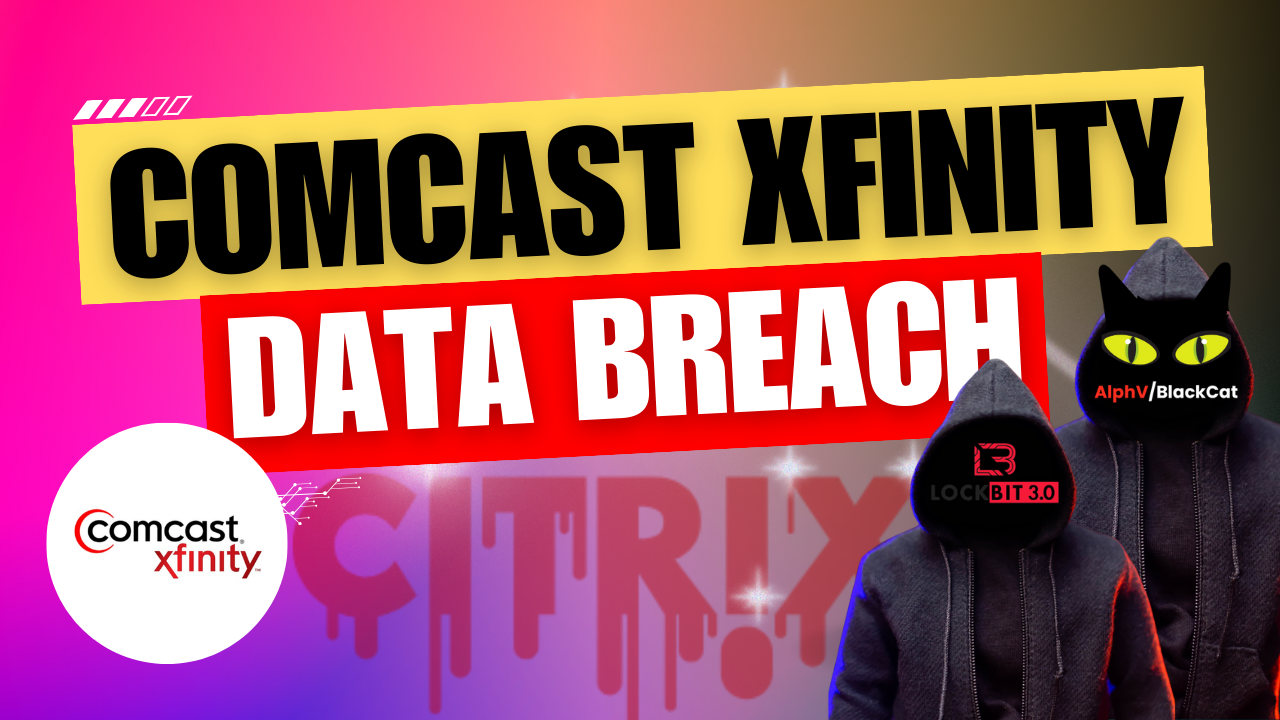
Comcast Xfinity Data Breach Exposes 36 Million Customers' Data
In a recent video, we discussed a significant data breach involving Comcast Xfinity, affecting nearly 36 million customers. The breach was linked to a ...
Xact IT Solutions

Top 2024 cybersecurity trends every business owner needs to know
Ignorance is not bliss when it comes to cybersecurity. In 2024, the cybercrime game is changing, and business owners who stay in the dark risk losing ...
Xact IT Solutions

Effortlessly import data from PC to Mac with Windows Migration Assistant
Making the switch from a PC to a Mac can be an exciting transition, but the prospect of transferring all your files and data may seem daunting. Fortunately, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Neurosurgeons of New Jersey Cyberattack: Lessons About Safeguarding Patient Data
In a recent turn of events, the Neurosurgical Associates of New Jersey, also known as the Neurosurgeons of New Jersey, fell victim to a cyberattack resulting ...
Xact IT Solutions

Must-have Android office apps to stay efficient on the go
Today, where remote work has become the new norm, having the right tools and apps can make all the difference in staying efficient and productive while ...
Xact IT Solutions

4 Questions to improve VoIP efficiency for the holidays
The holiday season brings with it an unavoidable challenge: the substantial increase in phone traffic that has the potential to overpower even the most ...
Xact IT Solutions

Disk Cleanup tool: What is it and how to use it
Keeping your computer running at peak performance is crucial to smooth business operations. Fortunately, there are plenty of methods and tools available ...
Xact IT Solutions
XACT IT SOLUTIONS INC

VF Corp, Owner of Vans and North Face, Cyberattack: What We Know So Far
VF Corp, the parent company of renowned brands Vans, Timberland, and North Face, recently fell victim to a cyber attack. The company, known for its clothing ...
Xact IT Solutions

Ditch the password pileup and unlock your apps with single sign-on
Juggling multiple passwords can be a frustrating burden, leading to the tempting yet risky shortcut of reuse. Single sign-on (SSO) offers the best of ...
Xact IT Solutions

How is telemedicine revolutionizing healthcare?
The worlds of technology and healthcare are colliding like never before, and telemedicine is leading the charge. This article breaks down how telemedicine ...
Xact IT Solutions

Fortifying your business against holiday cyberattacks
The festive season is upon us, but amidst the jingle bells and peppermint lattes lurks a silent threat: holiday hackers. As shopping sprees intensify ...
Xact IT Solutions

7 Tips to prevent VoIP downtime and ensure business continuity
Voice over Internet Protocol (VoIP) phone systems have become vital for business operations, so any downtime can have a significant impact on your organization. ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Adobe Users Targeted by Cybercriminals in Phishing Attacks
In 2024, we're shifting gears to address a pressing issue: a new breed of cybercriminals exploiting Adobe InDesign. This blog sheds light on their tactics ...
Xact IT Solutions

Why firmware updates are essential for business security
Firmware, the invisible but integral software that powers our devices, is often an overlooked aspect of a business’s cybersecurity strategy. This article ...
Xact IT Solutions

4-Step guide to choosing a Microsoft 365 plan for your business
The widespread adoption of Microsoft 365 by many businesses is understandable, given its extensive capabilities and numerous business benefits. However, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Supply-Chain Ransomware Attack Impacts 60 Credit Unions
A ransomware attack targeting a major technology provider in the financial services sector has sent shockwaves through the United States, affecting around ...
Xact IT Solutions

6 Must-try Firefox features
Are you ready to up your browsing game? Firefox is loaded with features designed for power users. Let’s explore the features that will turn you into ...
Xact IT Solutions
XACT IT SOLUTIONS INC
Healthcare Cybersecurity: Insights from Recent Hospital Cyber Attacks
On November 30, 2023, Capital Health fell victim to a cyber attack, resulting in network outages that disrupted their healthcare system in New Jersey. ...
Xact IT Solutions

Harness the holiday hype: Optimize your eCommerce store for peak season
Amidst the sea of eCommerce businesses vying for attention, it’s imperative that your brand stands out and offers a seamless, enjoyable shopping experience. ...
Xact IT Solutions

Holiday cybersecurity tips to protect against hackers
During the holiday season, it’s easy to lose focus on work-related responsibilities. Hackers may actively exploit the distractions that accompany this ...
Xact IT Solutions
XACT IT SOLUTIONS INC

How Much Should Business Leaders Pay For IT Support And IT Services?
"How much do you guys charge for your IT services?" This is one of the most common questions from prospective clients when they inquire about our services.
While ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Voice Scams Are Targeting Financial Leaders: Don't Be the Next Victim
As a leader in the financial service industry, cybersecurity can sometimes feel like a distant concern. We get it. You think of cyber attacks as something ...
Xact IT Solutions
XACT IT SOLUTIONS INC

7 Tech Tips for Business Leaders: Boosting Productivity in Financial Services
In the whirlwind pace of the financial services industry, where every second counts, maximizing efficiency and productivity is non-negotiable. Fortunately, ...
Xact IT Solutions

Why a solid-state drive (SSD) Mac upgrade is worth every penny
While the initial cost of a solid-state drive (SSD) may deter some Mac users, the long-term benefits and performance gains of SSDs far outweigh the upfront ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Out With The Old, Get Ready For The New Year: Debunking 5 Common Cybersecurity Myths
In today's super-connected world, keeping your business safe from cyber threats is a big deal. As we navigate the ever-changing digital landscape, ...
Xact IT Solutions

Erase with ease: A guide to securely wiping your Android device
Before you decide to sell, donate, or discard your old Android device, it’s important to make sure that all your personal or business data stored on ...
Xact IT Solutions
XACT IT SOLUTIONS INC

When Your Facebook Or Other Online Account Gets Hacked, Who’s Responsible For The Losses?
Recently, the CEO of a very successful marketing firm had their Facebook account hacked. In just one weekend, the hackers pulled off a heist, running ...
Xact IT Solutions

Microsoft Teams and Google Meet: A comparison of video conferencing platforms
Remote collaboration and virtual meetings have skyrocketed due to the increase in telecommuting. To facilitate face-to-face communication, companies ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Fidelity National Financial Cyber Attack: What We Know So Far
Today, I want to shed light on a recent cyber attack that hit a Fortune 500 Real Estate title insurance and settlement services company. It's crucial ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Protecting Your Finances: Latest Cybersecurity Threat for Businesses in Philadelphia
There's a new cyber threat in town, and it's targeting banks, financial institutions, and cryptocurrency wallets in the greater Philadelphia area.
Remember ...
Xact IT Solutions

How to fix Windows 10/11 printing problems
Printing issues can be exceptionally exasperating. Just as you urgently have to print a hard copy of a document, some problem arises. This frustration ...
Xact IT Solutions
XACT IT SOLUTIONS INC

How Effectively Managing Risk Bolsters Cyber Defenses
In today’s rapidly evolving digital landscape, where cyber threats and vulnerabilities continually emerge, it’s obvious that eliminating all risks ...
Xact IT Solutions
XACT IT SOLUTIONS INC
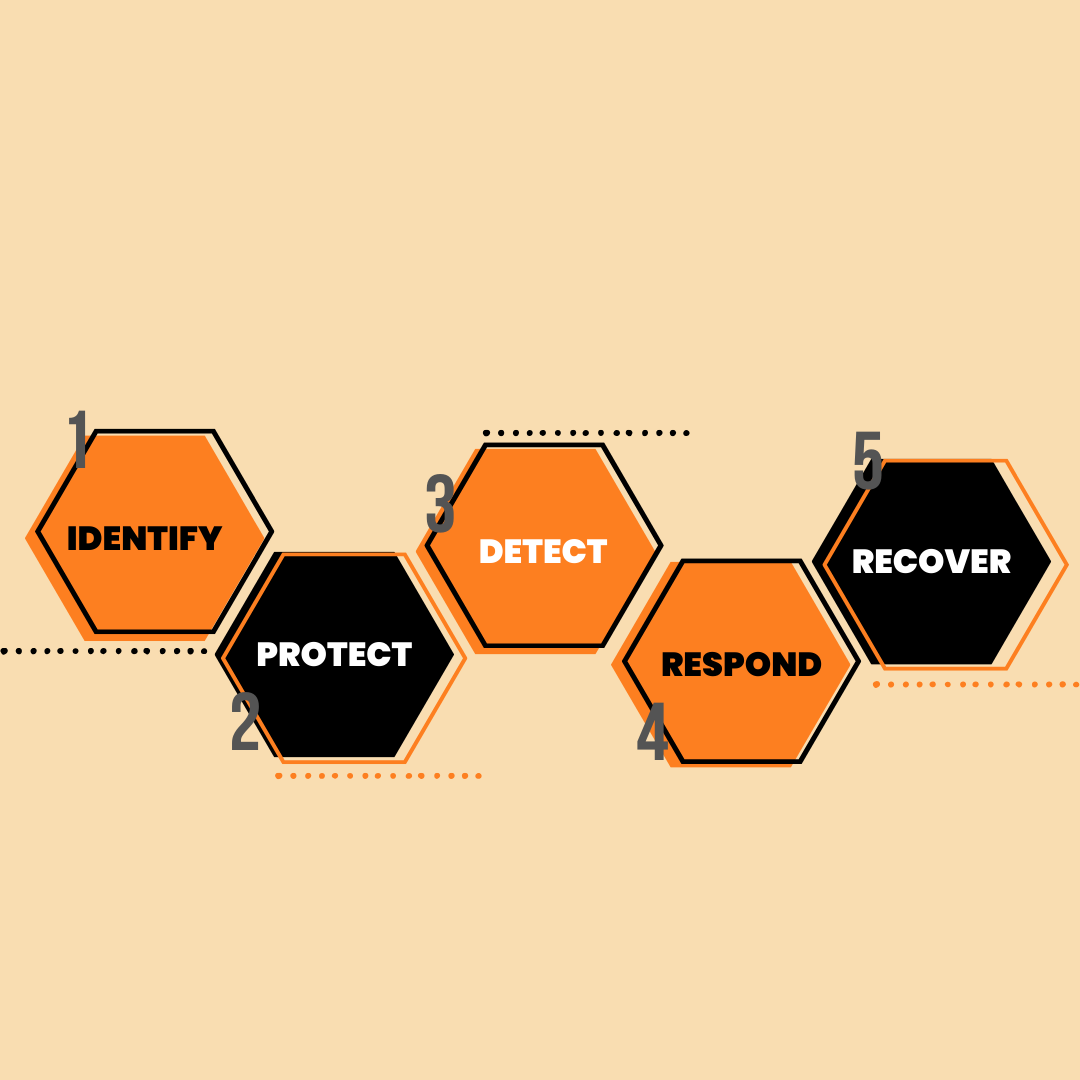
How to Achieve Strategic Cyber Risk Management With NIST CSF
Securing sensitive data and safeguarding critical technology from cyber threats is vital for businesses, such as yours. The survival and growth of your ...
Xact IT Solutions
XACT IT SOLUTIONS INC
Feasting Safely: A Cybersecurity Guide for Thanksgiving Weekend
As the Thanksgiving weekend approaches, our minds are filled with thoughts of turkey, pumpkin pie, and quality time with loved ones. However, amid the ...
Xact IT Solutions

Powering productivity: The optimal internet speed for remote work
For employees working remotely, a reliable and robust internet connection has become indispensable. However, with a vast array of internet plans and ...
Xact IT Solutions

Choosing the right EHR hardware for your practice
The right electronic health record (EHR) hardware can make your practice more efficient, productive, and secure. It can streamline your workflow, improve ...
Xact IT Solutions

Don’t fall for these common social engineering tricks
In an ever-evolving cybersecurity landscape, experts tirelessly develop new defense systems to safeguard individuals and businesses from the relentless ...
Xact IT Solutions
XACT IT SOLUTIONS INC

How To Have The Freedom To Do What You Want When You Want In Your Business
Could you step away from your business for a month, and come back and have it running and growing and profitable? What about 6 months? A year? This ...
Xact IT Solutions

Setting up a guest Wi-Fi network in your office
Does your office regularly get visitors? Chances are that many of these visitors ask to connect to your Wi-Fi for different reasons. In any case, an ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Top Technologies Driving Digital Transformation
When creating your business budget, don't just see technology costs as operational expenses—view them as investments propelling your organization ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Top Digital Transformation Myths Debunked
In the fast-paced landscape of today's business world, digital transformation stands out as a crucial element for success. Its potential to attract new ...
Xact IT Solutions

Things to consider when deciding between cloud and on-premises VoIP systems
The decision to adopt Voice over Internet Protocol (VoIP) systems is a transformative step for any business, enhancing communication, collaboration, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Siri Co-Founder To Reveal The Coming AI Revolution And How To Harness It
Imagine asking your phone a question and having it immediately understand and help accomplish your request. For most people, this vision became a ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Navigating the Fallout: Mr. Cooper’s Cyber Attack
On the eerie night of Halloween, instead of the expected scares and pranks, Mr. Cooper found itself plunged into a real-life nightmare—a massive cyber ...
Xact IT Solutions

Securing Microsoft 365: A guide to mitigating key risks
With more and more businesses shifting toward cloud computing solutions such as Microsoft 365, understanding the potential security risks and how to ...
Xact IT Solutions
XACT IT SOLUTIONS INC

FTC Safeguard Rule Amendment: What It Means for Your Financial Data
The Federal Trade Commission (FTC) has just introduced a significant amendment to its safeguard rule, which has far-reaching implications for non-banking ...
Xact IT Solutions

Proven business continuity strategies to safeguard your operations
Businesses operate in a volatile world where unforeseen events such as cyberthreats and natural disasters can strike at any moment. To ensure your company’s ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Unpacking the Ace Hardware Cyber Attack: A Major Disruption in Hardware Retail
Ace Hardware, a renowned cooperative retailer, recently fell victim to a major cyber attack that has sent shockwaves through its extensive operations. ...
Xact IT Solutions
XACT IT SOLUTIONS INC
Recent Cybersecurity Attacks: Lessons for Businesses
Businesses face constant threats from cybercriminals who are always looking for ways to exploit vulnerabilities. Recent cyberattacks on major corporations ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Boeing Faces Cybersecurity Threat from LockBit Ransomware Group
The world's leading aerospace and defense company, Boeing, recently found itself in the crosshairs of one of the most notorious cybercriminal gangs, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

The Impact of SEC Cybersecurity Rules on Businesses: Lessons from the Clorox Hack
In this blog, we're diving into the world of cybersecurity regulations and their profound effects on businesses in the United States. While we've previously ...
Xact IT Solutions

5 Tips for secure customer data collection
Much of business centers on giving people what they want. This means understanding customers’ interests and needs by accumulating and organizing customer ...
Xact IT Solutions
XACT IT SOLUTIONS INC

A Shark’s Eye View Of The Future Of Small Business Tech
In an exclusive interview, Shark Tank celebrity Robert Herjavec will share his unique insights on technology, automation, cybersecurity, and much more ...
Xact IT Solutions

How to boost cybersecurity when working remotely
Remote work has become the norm, and it brings a host of benefits to both employees and employers. However, working outside of a traditional office environment ...
Xact IT Solutions
Effective malware removal tips for Android devices
Because the Android operating system is open source, programmers find it easy to customize it and develop applications for it. However, it’s this same ...
Xact IT Solutions

What makes VoIP phishing cybercriminals’ weapon of choice?
Voice over Internet Protocol (VoIP) phishing, a technique that involves manipulating VoIP technology to trick users into giving up sensitive information, ...
Xact IT Solutions

Shaping future workforces with the human cloud
The future of work is here, and it’s digital, dynamic, and decentralized. The human cloud, often likened to the gig economy, is a pivotal force behind ...
Xact IT Solutions

10 Essential tricks for a speedier Windows 11 experience
As a business owner, you’re always searching for ways to streamline your workflow and increase productivity. One way to boost efficiency is by optimizing ...
Xact IT Solutions

HIPAA and IT: The 4 key factors
There is a reason medical records are regarded as confidential. In addition to general respect for privacy, their illicit disclosure has caused social ...
Xact IT Solutions

Facebook and Twitter privacy settings: Everything you need to know
Facebook and Twitter are two of the most popular social media platforms in the world. Both of these platforms collect a lot of personal data that can ...
Xact IT Solutions

Laptops vs. desktops: Which one is right for your small business?
When you’re running a small business, every dollar counts. That’s why it’s important to make wise choices when it comes to purchasing computers. ...
Xact IT Solutions

Which is better for your business, Microsoft Teams or Google Meet?
With so many online communication tools available, choosing the right one for your business can be daunting. But two platforms stand out in terms of ...
Xact IT Solutions

Tips to enhance your Excel proficiency
Excel, a widely used office tool, holds immense potential that often remains untapped by many users. If you’re struggling with Excel, this guide provides ...
Xact IT Solutions

Follow these steps to fortify your data in the cloud
As the world becomes more interconnected, the importance of securing sensitive information stored in the cloud becomes even more paramount. Cyberthreats ...
Xact IT Solutions

The 5 most common data backup solutions
For any business, data is more than just information; it’s an invaluable asset that drives decision-making and strategy. Losing data can result in ...
Xact IT Solutions
XACT IT SOLUTIONS INC

What is a Password Manager?
Many people still use easily guessable passwords like "password123" or "123456." These passwords are a piece of cake for hackers using automated tools ...
Xact IT Solutions

Are your passwords strong enough?
While there are many security measures one can take, the most basic but also crucial step in protecting your online presence involves creating strong ...
Xact IT Solutions

5 Reasons why you shouldn’t jailbreak your iPad
While many iPad users enjoy their devices as standard, there are those who want non-App Store apps and modifications to their devices outside what Apple ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Top AI Cyber-Risks to Be Aware Of
The advent of AI has ignited a revolution, captivating both industry giants and smaller businesses alike.
However, in the midst of celebrating AI's ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Preserving Your Business: Avoiding the Pitfalls of Social Media Misuse
The widespread adoption of social media has brought about a profound change in the way we communicate and conduct business. Yet, this surge in popularity ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Phishing Scams: What You Need to Know
Phishing scams rank among the most pervasive and effective forms of cyberattacks. Recognizing the significant danger they present ...
Xact IT Solutions

Why HTTPS is essential for online security
Cybercriminals are relentless in coming up with new ways to steal our personal information and financial data. That’s why it’s more important than ...
Xact IT Solutions

Don’t let your VoIP calls be intercepted: Here’s how to protect yourself
VoIP eavesdropping is a serious security threat that can have devastating consequences for businesses and individuals. This blog post will provide you ...
Xact IT Solutions

Leverage mobile threat detection (MTD) for enhanced business security
With the rise of remote and hybrid work, the workplace has become bigger than the four walls of traditional office spaces. Employees now access sensitive ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Vulnerability Management: Expert Guidance Made Simple
In today's fast-paced digital landscape, the security of your business is of paramount importance. Whether you're a decision maker, an IT professional, ...
Xact IT Solutions

The role of mobile device management in healthcare
Mobile devices have become indispensable tools in the healthcare industry. Doctors, nurses, and other healthcare workers use mobile devices to access ...
Xact IT Solutions

Enhancing business security: The role of two-factor authentication and two-step verification
Threats lurk in every corner of the digital space, and businesses need to take extra steps to safeguard their data from malicious actors. Fortunately, ...
Xact IT Solutions

A simple guide to choosing the ideal office Wi-Fi router
A reliable Wi-Fi network is the backbone of any modern office, enabling productivity and connectivity. Selecting the right office Wi-Fi router is crucial ...
Xact IT Solutions

5 Questions to ask before upgrading to VoIP
Voice over Internet Protocol (VoIP) services are revolutionizing the way businesses communicate by providing organizations with effective and consistent ...
Xact IT Solutions

Unleash the power of Microsoft 365’s Bookings feature
Microsoft Bookings is a scheduling app that allows you to create a website where customers can book in-person or virtual appointments with your business. ...
Xact IT Solutions

How SaaS saves businesses money
Software is a key component of business IT. However, software-related expenses can quickly eat into your budget. Thankfully, there’s a solution that ...
Xact IT Solutions

How email automation can benefit your business
Email marketing is an effective way to reach your target audience and promote your business. But if you’re not automating your email campaigns, you’re ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Best Practices for Effective Disaster Preparedness Planning
A well-prepared disaster plan is a lifeline for businesses in times of crisis. However, what many businesses fail to realize is that a robust disaster ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Four Ways Disasters Fuel Cyberattacks
In today's technology-driven world, businesses face a multitude of challenges. However, the aftermath of an unexpected disaster can push organizations ...
Xact IT Solutions

The power of IT security audits in safeguarding your business
Cyberattacks are becoming increasingly sophisticated, making it crucial for business owners to proactively safeguard their sensitive information. One ...
Xact IT Solutions

Easy ways to lock your Mac when you’re away from keyboard
It’s a security risk to leave your Mac unlocked when you’re away from your desk. Anyone could simply use it to access your accounts, files, or personal ...
Xact IT Solutions

How to avoid WordPress website issues
WordPress is a popular platform for building websites, but like any other software, it can have its share of issues. In this article, we’ll go over ...
Xact IT Solutions

Revolutionizing communication: The impact of 5G on VoIP systems
Are you a business owner looking to improve your VoIP (Voice over Internet Protocol) systems? With 5G technology, there are now more opportunities ...
Xact IT Solutions

Simplify your workflow with these Windows 11 keyboard shortcuts
Did you know that Windows 11 has a bunch of shortcuts that can make your life easier and help you get things done more quickly? We’ve put together ...
Xact IT Solutions

How to get the most out of your Android tablet
Android tablets are great devices for productivity, entertainment, and communication. However, over time, they can become slow and unresponsive due to ...
Xact IT Solutions

AI is changing the healthcare industry
All indications point to artificial intelligence (AI) being a game changer for the healthcare industry. And, in fact, it has already revolutionized healthcare ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Navigating the New Cybersecurity Landscape: Understanding the Impact of SEC Rules
The US Securities and Exchange Commission (SEC) has introduced a fresh set of cybersecurity regulations. In this blog post, we're diving deep into the ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Safeguarding Your Digital World: A Comprehensive Guide to Cybersecurity
In the rapidly evolving landscape of today's digital age, cybersecurity has emerged as a paramount concern. As we witness the growing prevalence of cyber ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Unlocking Better Business Outcomes: The Perfect Blend of Compliance & Cybersecurity
Compliance and security? They embody a relationship akin to best of friends, mutually safeguarding one another's interests, yet distinctively demonstrating ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Unlocking Compliance: Safeguarding Your Business with a Solid BIA Plan
We get it – keeping your ship sailing smoothly through the digital seas while staying on the right side of the law can feel like juggling flaming ...
Xact IT Solutions

What to consider when choosing a VPN solution
Everyone from cybercriminals to government agencies can attempt to monitor and access your data on the internet. To protect yourself, you need a virtual ...
Xact IT Solutions
XACT IT SOLUTIONS INC
Exploring the Pros and Cons of Managed IT Service Providers – A Balanced View
Curious about teaming up with a Managed Service Provider (MSP) but feeling a bit uncertain? Fret not! We're here to provide a straightforward rundown ...
Xact IT Solutions

The ultimate guide to mobile device security for businesses
Mobile devices allow employees to work remotely, communicate effectively, and access important data. However, mobile devices also pose significant cybersecurity ...
Xact IT Solutions

Business essentials for battling VoIP theft of service
Voice over Internet Protocol (VoIP) offers cost-effective and flexible communication solutions. However, with its benefits come potential risks, one ...
Xact IT Solutions

Outlook tips to help you get more done
Microsoft Outlook is a popular email and calendaring tool that is used by all types of businesses. It is easy to use and convenient, and it has many ...
Xact IT Solutions

Debunking misconceptions about cloud computing
Cloud computing has changed the way companies operate by offering cost-effective, scalable, and flexible solutions.However, there are some misconceptions ...
Xact IT Solutions

Costly business continuity plan mistakes to steer clear of
A solid business continuity plan (BCP) is crucial for safeguarding your company against potential disruptions and ensuring resilience in the face of ...
Xact IT Solutions

Protecting your SMB from cyberattacks: Know your enemy
Small and medium-sized businesses (SMBs) often face challenges in protecting their IT systems from cyberattacks. One of the most important steps that ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Three Essential Cybersecurity Solutions for Small Businesses: Important Considerations
Most organizations make cybersecurity overly complicated because “you should do it either way.” This is not a valid argument. Business owners have ...
Xact IT Solutions

Optimizing cloud costs for business success
Cloud computing offers unparalleled benefits in terms of scalability, flexibility, and accessibility to businesses worldwide. However, without careful ...
Xact IT Solutions
XACT IT SOLUTIONS INC

5 Top Cybersecurity Threats: An Executive's Guide
Business Cybersecurity is serious; an ever-present threat that executives are right to worry about.
But understanding the top cybersecurity threats ...
Xact IT Solutions

How to engage audiences through video content
Video marketing has emerged as a powerful strategy for promoting brands, services, and products and achieving various goals, such as driving sales, increasing ...
Xact IT Solutions
XACT IT SOLUTIONS INC

The Importance of Fortifying Employee Security Awareness in Your Business
In the modern world, organizations are growing more conscious of the constantly evolving cybersecurity landscape. They are investing significant resources ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Mistakes that Sabotage Employee Cybersecurity Training
In a rapidly evolving threat landscape, employee cybersecurity training is crucial. It acts as the frontline defense against cyberattacks, helping ...
Xact IT Solutions

A guide to eliminating clutter on your PC
Managing clutter on your desktop and hard drive is essential for maintaining peak computer performance. In this article, we will explore five common ...
Xact IT Solutions
XACT IT SOLUTIONS INC

The State of Cybersecurity: Are We Falling Behind?
In the fast-paced digital age, cybersecurity has become a critical concern for both governments and businesses. With cybercriminals relentlessly targeting ...
Xact IT Solutions

Important cybersecurity terms every business owner should know
As technology advances, so do the risks associated with cyberthreats. Understanding basic cybersecurity terms is essential for business owners to protect ...
Xact IT Solutions

How technology is revolutionizing healthcare
From the widespread adoption of electronic health records for seamless data management to artificial intelligence-driven diagnostics and telehealth services, ...
Xact IT Solutions

Leverage thin and zero clients to slash IT costs
If escalating IT costs are burning a hole in your organization’s budget, it’s time to explore a game-changing approach: thin and zero clients. By ...
Xact IT Solutions

Leveraging call recording for business improvement
Call recording has become essential in the business world today. With the advancement of technology, businesses can now automatically record and analyze ...
Xact IT Solutions

Your essential guide to Microsoft Whiteboard
In the age of remote work and distributed teams, effective collaboration and visual communication are vital for business success. Microsoft Whiteboard ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Building a Strong Cybersecurity Awareness Training Program for Your Business
Cybersecurity awareness is crucial for businesses to protect their sensitive data and prevent cyber attacks. However, many companies are falling short ...
Xact IT Solutions

Cloud service models: Which one is right for your business?
If you’re in the market for cloud services, you’ve probably already realized that there is no one-size-fits-all cloud solution for businesses. Every ...
Xact IT Solutions

Essential guide for mitigating data loss
Data loss can have severe consequences, including financial loss, reputational damage, and legal issues. Therefore, implementing robust measures to safeguard ...
Xact IT Solutions

How AI transforms Microsoft Bing and Edge into your web copilot
AI-powered Microsoft Bing and Edge have revolutionized the way we interact with the digital world. With the power of artificial intelligence (AI) at ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Why Every Business Needs a Solid Business Continuity Plan
Managing a business is tough. It can be overwhelming, with constant demands pulling you in various directions. It's easy to get caught up in the daily ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Data Loss Disasters that can Hurt your Business
Data loss disasters can take many forms.
Data loss disasters can happen in many ways, like natural disasters, cyberattacks, or simple human mistakes. ...
Xact IT Solutions

Strengthening SMB cybersecurity with managed IT services
As technology continues to advance, small- and medium-sized businesses (SMBs) face increasing cybersecurity risks. Protecting sensitive data and maintaining ...
Xact IT Solutions

The importance of disabling location settings on your Android device
It’s easy to overlook the potential risks of leaving your Android device’s location settings on. However, it’s crucial to understand the implications ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Clop Ransomware Group: A Major Threat to Cybersecurity
The Clop ransomware group gained significant notoriety in 2023 as one of the most prolific cybercriminal organizations. They have exploited various ...
Xact IT Solutions

How to keep your Mac safe
Many users believe that Mac laptops and desktops are more secure than Windows devices. However, Macs are still susceptible to cyberthreats, and they’re ...
Xact IT Solutions

Exploring the advantages of dual monitors
Are you tired of constantly juggling between different windows on your computer? Dual monitors can be the game-changer you need to overcome such challenges. ...
Xact IT Solutions

Get The IT Help You Deserve
5 Questions You Should Hear ‘Yes’ To
As a business owner, you likely carefully vet every employee you hire to work for your business. You inspect ...
Xact IT Solutions

VoIP vs. VoLTE: Which is right for you?
When it comes to modern communication technologies, Voice over Internet Protocol (VoIP) and Voice over Long-Term Evolution (VoLTE) are two popular options ...
Xact IT Solutions
XACT IT SOLUTIONS INC

The Changing Landscape of Cybersecurity: Navigating New State Laws and Regulations
In this post, we're going to delve into a topic that has been creating ripples in the cybersecurity industry, government bodies, and various industries: ...
Xact IT Solutions
Streamline your operations with Microsoft update channels
Microsoft update channels provide users with diverse options to receive software updates. Whether you are an individual user, a small business, or a ...
Xact IT Solutions
XACT IT SOLUTIONS INC
The Benefits of Outsourced IT: How it Can Streamline Your Business Operations
First, let's define who an "outsourced IT" support is.
An outsourced IT support is a team of experts who provide technical assistance to businesses from ...
Xact IT Solutions

6 Essential cloud solutions for small businesses
Cloud technology has undoubtedly become an indispensable aspect of computing in recent years. Nevertheless, some small- to mid-sized businesses (SMBs) ...
Xact IT Solutions
XACT IT SOLUTIONS INC

How to Choose the Best Outsourced IT Service for your Business
Businesses heavily rely on technology to streamline their operations and gain a competitive edge. However, managing an entire IT infrastructure in-house ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Debunking Outsourced IT Myths (Why Outsourcing IT is the Way to Go)
Outsourced IT acts as a beacon of relief, allowing you to offload the burdensome responsibilities of managing IT. With dedicated professionals and ...
Xact IT Solutions
XACT IT SOLUTIONS INC

The Truth About Cyber Insurance for Businesses (Why you should NOT rely on it alone)
In this article, we aim to dispel a common misconception among business owners regarding cybersecurity – the belief that cyber insurance alone is sufficient ...
Xact IT Solutions

How business intelligence drives success
Business intelligence (BI) encompasses a wide range of techniques and technologies that enable organizations to harness their data to gain valuable insights. ...
Xact IT Solutions

Optimize your system through defragmentation
We rely on our computers to function smoothly and effectively, whether we’re using them for personal tasks or professional pursuits.. However, over ...
Xact IT Solutions

Unveiling the invisible threat: Exploring the world of fileless malware
With its ability to evade traditional antivirus solutions, fileless malware poses a significant challenge to organizations and individuals alike, as ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Don't Fall for These 5 Sneaky Social Engineering Attacks
Social engineering attacks prey on human vulnerabilities, manipulating people into unknowingly divulging sensitive information or performing actions ...
Xact IT Solutions

Selecting the perfect health app or wearable for your needs
The rise of health apps and wearable tech has empowered individuals to take an active role in monitoring and improving their health. These devices and ...
Xact IT Solutions
XACT IT SOLUTIONS INC

What is Biometric Voice Authentication and How Does It Work?
A world where your voice becomes your unique identifier - unlocking doors, accessing your accounts, and verifying your identity with a simple phrase.
Well, ...
Xact IT Solutions

How to choose the right keyboard for your needs
From the layout and key mechanism to additional features and customization options, there are numerous factors to consider when selecting a computer ...
Xact IT Solutions
XACT IT SOLUTIONS INC

5 Cybersecurity Tips for Small Businesses (Easy to Implement)
Everything seems all too well in your business - you're bringing in new clients and increasing your profit each month. However, you find that as your ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Strengthening Healthcare Cybersecurity: Protecting Hospitals from Rising Cyber Attacks
Just recently, both Idaho Falls Community Hospital and Mountain View Hospital fell victim to a massive cyber attack, suspected to be a ransomware event. ...
Xact IT Solutions

How are business phone systems different today?
Business phone systems have undergone significant transformations, adapting to the evolving needs of modern enterprises. Gone are the days of traditional ...
Xact IT Solutions
ALLEN PAJAR

Exploring the advantages of Microsoft Delve
Imagine a tool that understands your work preferences, anticipates your information needs, and effortlessly finds relevant content without any manual ...
Xact IT Solutions
ALLEN PAJAR

Why hybrid cloud solutions matter
Hybrid cloud solutions are becoming increasingly popular because they offer numerous benefits to businesses of all sizes. By combining the capabilities ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Achieve DFARS Compliance
Safeguarding Controlled Unclassified Information (CUI) has recently become a top priority for the Department of Defense. To establish a standardized approach, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Interim DFARS Rule: What It Means for You
The Defense Federal Acquisition Regulation Supplement (DFARS) incorporated the Cybersecurity Maturity Model Certification (CMMC) in January 2020, which ...
Xact IT Solutions
XACT IT SOLUTIONS INC

CMMC Compliance Checklist
If someone claims to have an easy solution for all your CMMC-related problems, they are most likely trying to deceive you. The CMMC is a complex initiative ...
Xact IT Solutions
BOOM ITTIPRATEEP

From data to success: Leveraging dashboards for business growth
Businesses must not only collect data but also be able to analyze it effectively in order to make informed, data-driven decisions. This is where dashboards ...
Xact IT Solutions
ALLEN PAJAR

Improving productivity: How to disable disruptive Windows 11 settings
With every new update, Windows 11 brings a range of new features and enhancements to improve user experience. However, it also introduces some disruptive ...
Xact IT Solutions

Your guide to dealing with distributed spam distraction
Distributed spam distraction (DSD) is a sophisticated cyberattack employed by malicious actors to steal valuable information from businesses. But unlike ...
Xact IT Solutions

A guide to verifying Android apps
Verifying the authenticity and safety of apps before installing them is crucial to protect your device and personal information. There are numerous malicious ...
Xact IT Solutions

Upgrading your Mac: The key indicators to consider
Upgrading to a new Mac can bring a host of benefits, from improved performance and enhanced features to better compatibility with the latest software ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Stay Ahead of AI Cybersecurity Threats
While artificial intelligence (AI) offers many benefits to businesses, it has also created new vulnerabilities that cybercriminals can exploit to launch ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Artificial Intelligence in Business
In today's highly competitive business landscape, businesses are turning to artificial intelligence (AI) to gain an edge by boosting efficiency, productivity, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Unmasking the Royal Ransomware Group: Tactics and Countermeasures
The Royal Ransomware Group has emerged as one of the most prolific ransomware groups since September 2022. In this blog post, we will discuss their activities, ...
Xact IT Solutions

Questions to consider before replacing your servers
When it comes to replacing your company’s servers, you should review aspects of your existing server infrastructure and consider the implications of ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Why You Need A Cybersecurity Plan: Lessons from the Philadelphia Inquirer Attack
The Philadelphia Inquirer, one of the largest newspapers in the nation, has recently fallen victim to a cyber-attack. As a native of Philadelphia, this ...
Xact IT Solutions

Improving your business’s on-hold strategy with VoIP
For businesses, the on-hold experience can either be a missed opportunity or a chance to showcase professionalism and exceptional customer service. With ...
Xact IT Solutions

Microsoft Loop in Outlook and Teams: Streamlining communication and productivity
Microsoft Loop is a new tool that allows you to streamline your team’s workflows and make collaboration more efficient without switching between different ...
Xact IT Solutions

Help Your Business Thrive With Co-Managed IT Services
Over the past few years, awareness about IT services has significantly increased. Businesses of varying sizes recognize the need for and importance of ...
Xact IT Solutions

Get Ready To Maximize Efficiency With Help From Co-Managed IT Services
IT services are necessary for every business in the country – IT companies help businesses protect their data, ensure day-to-day operations run smoothly, ...
Xact IT Solutions

Simple speed hacks to boost your Chrome browser
Google Chrome is the go-to browser for many users because of its user-friendly interface and robust features. However, some users have reported that ...
Xact IT Solutions

Staying afloat: The importance of a business continuity plan for SMBs
As a small- or medium-sized business (SMB) owner, you understand how challenging it can be to keep your company afloat. While you may have a solid business ...
Xact IT Solutions
Hassle-free login process with Windows Hello in Windows 11
Logging in to your Windows 11 computer can be a hassle, especially when you have to remember and enter a complex password every time. Windows Hello is ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Why Password Security Matters: Protecting Your First Line of Defense
Passwords are the first line of defense against unauthorized access to your online accounts. Whether it's your email, social media, or banking account, ...
Xact IT Solutions

How to enhance your company’s BYOD security
Bring your own device (BYOD) is a trend that has grown in popularity because of the convenience it offers employees, but it also presents a serious security ...
Xact IT Solutions
BOOM ITTIPRATEEP

Microsoft Teams Productivity Tips Every Small Business Needs To Know
Every business needs the right tools to get the job done and to keep your team on track. But juggling multiple apps and software can be a nightmare ...
Xact IT Solutions
BOOM ITTIPRATEEP

How to Eliminate 10 Common Tech Problems Forever
They say, “You get what you tolerate” and now more than ever, we’ve been conditioned to tolerate worse service at higher prices. Companies get ...
Xact IT Solutions
XACT IT SOLUTIONS INC

How Hackers Are Using AI to Carry Out Sophisticated Cyber Attacks
AI analyzes and guesses passwords using deep learning techniques such as Generative Adversarial Networks (GANs), language models, and deep latent variable ...
Xact IT Solutions

Transform your healthcare practice with online scheduling
As the healthcare industry continues to evolve, so do patient expectations. Aside from receiving high-quality care, patients now also expect convenient ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Why Now Is The Time To Embrace Zero Trust Cybersecurity
Zero trust security helps safeguard your business against today's mounting cyber-attacks and security challenges. Through continuous authentication and ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Steps to Adopting Zero Trust Security
As cyberattacks continue to evolve in frequency and sophistication, organizations like yours need a cybersecurity approach that can keep these threats ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Zero Trust Security Myths You Shouldn't Believe
In today's threat landscape, cyberattacks are a constant danger. By adopting a zero-trust security model, you can protect your network and maintain data ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Here's How to Establish a Zero-trust Cybersecurity Strategy for Your Small Business
Cyberattacks are on the rise and have become more sophisticated. A simple lapse in your network security could lead to a chain of events that could prove ...
Xact IT Solutions

Easy solutions for common networking problems
Network errors can be frustrating and can disrupt your productivity. They can be caused by a variety of factors, including hardware failures, software ...
Xact IT Solutions
XACT IT SOLUTIONS INC
CommScope Hit by Ransomware: Employee Data and Proprietary Information Leaked
CommScope is a global network infrastructure provider that designs and manufactures connectivity and communication solutions for businesses and organizations.
A ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Spartanburg County Hit by Ransomware Attack: Lessons Learned for Businesses and Governments
Spartanburg County is situated in the northwestern region of South Carolina, covering an area of around 819 square miles (2,122 square kilometers).
Spartanburg ...
Xact IT Solutions
XACT IT SOLUTIONS INC
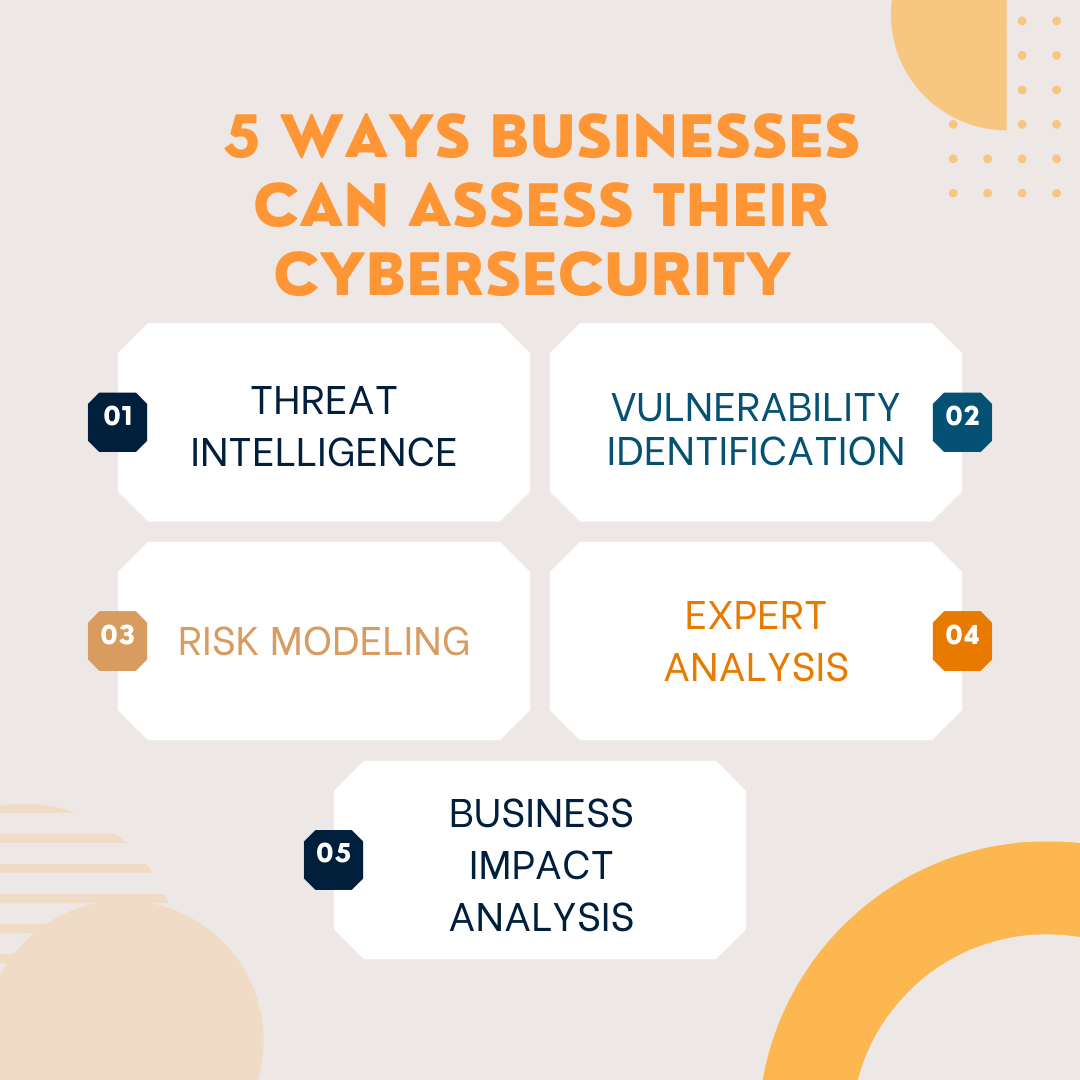
5 Ways Businesses Can Assess Their Cybersecurity
As cyber threats continue to increase, it's important for businesses to understand their vulnerabilities and prepare accordingly. But where do businesses ...
Xact IT Solutions

Here’s how to fix the most common VoIP issues
A piece of technology that claims to cut your expenses in half may seem too good to be true, and often, it is. But this isn’t the case with Voice over ...
Xact IT Solutions
ALLEN PAJAR

When to use Groups, Teams, and Yammer
In the digital age, businesses and organizations have a variety of collaboration tools at their disposal. With so many options available, it can be ...
Xact IT Solutions

Cloud ERP: Streamlining your business operations in the digital age
The cloud has revolutionized the world of enterprise resource planning (ERP), enabling companies to access their ERP software and data from any location ...
Xact IT Solutions

Protect your business with a disaster recovery plan
No organization wants to experience the nightmare of losing valuable customer data, financial records, or confidential documents. Unfortunately, unless ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Should You Stop Using Public USB Charging Stations? Insights from the FBI Warning
Tweet from the FBI warning against the use of public USB ports.
The FBI Denver office recently warned Americans against using USB charging stations ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Ransomware Attack Hits NCR's Aloha POS, Leaving Thousands of Restaurants Unable to Access Back Office Tools
Recently, Aloha POS, a software system used by over 100,000 restaurants and run by its parent company, NCR, was reportedly taken down in a ransomware ...
Xact IT Solutions

Essential tips for maximizing Windows 11 after installation
The default settings of Windows 11 may not be specifically tailored to your needs, and it can contain several bothersome elements that can ruin user ...
Xact IT Solutions

Does password autofill make hacking easier?
Password autofill is undeniably convenient, but do you know the dangers of using this common browser feature? Here’s what you should be aware of when ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Why Outsource your Cybersecurity?
In safeguarding your business against cyberattacks, using appropriate tools and technology is only a portion of the solution.
It's equally important ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Compliance Standards: The Critical Factor in Business Success
Ensuring the success of a business involves more than just developing a great product or service and hiring competent staff. Compliance with industry ...
Xact IT Solutions
XACT IT SOLUTIONS INC

5 Types of Risks Your Cybersecurity Risk Assessment Needs to Identify
As the world becomes more digitally dependent, businesses are facing a greater need to protect their systems and data from cyber-attacks. This is where ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Understanding the Importance of Cybersecurity Risk Assessments
Today, risk assessment is one of the most important factors in the process of ensuring the cybersecurity of any firm. In this post, we'll go over what ...
Xact IT Solutions

5 Essential steps to defend against insider threats in healthcare
Among the most pressing issues that the healthcare sector must grapple with are insider threats. To protect confidential records, financial information, ...
Xact IT Solutions

5 Tips to boost your desktop productivity
Working on a computer all day can be tedious and tiring. And doing the same things over and over again can affect your morale, which, in turn, can impact ...
Xact IT Solutions

The Importance of VoIP Quality of Service for business communication
Quality of Service (QoS) is crucial when selecting a Voice over Internet Protocol (VoIP) provider, as you may experience call quality issues even with ...
Xact IT Solutions
Making smarter strategic decisions with Power BI
Making the right business strategies relies heavily on data analysis and timely insights. With Microsoft Power BI, businesses can access vast amounts ...
Xact IT Solutions

Protect your business with these secure web browsers
One of the most common ways cybercriminals gain access to business networks is through unsecured web browsers. Cybercriminals can exploit vulnerabilities ...
Xact IT Solutions
XACT IT SOLUTIONS INC
Is Your Current IT Company Doing Their Job?
Is Your Current IT Company Doing Their Job? Take this Quiz to Find Out.
If your current IT company does not score a “Yes” on every point in this ...
Xact IT Solutions
XACT IT SOLUTIONS INC
How do Cybercrimes Ruin Companies? Let’s Count the ways.
The consequences of a successful cyberattack can be catastrophic for a business, ranging from reputational damage to financial loss and even bankruptcy.
In ...
Xact IT Solutions
XACT IT SOLUTIONS INC
The Cyber Crisis Faced by Small and Medium-Sized Businesses
You Will Probably be Called STUPID. . . or IRRESPONSIBLE
Should You Fall Victim to Cyber Attack
Isn't it incredibly unjust? Victims of crimes such as ...
Xact IT Solutions
XACT IT SOLUTIONS INC

The Shocking Truth: How Hackers Can Infiltrate Your Email Accounts Without Your Password or Username
It may come as a shock to discover that hackers can infiltrate your Gmail or Microsoft 365 email accounts without needing your username or password, effortlessly ...
Xact IT Solutions
Why your business needs to embrace new technology
Many businesses today rely on new technology to enhance productivity, facilitate efficient communication with clients, and ensure steady growth. At the ...
Xact IT Solutions

3 Reasons not to bypass Windows 11’s TPM requirement
Microsoft released Windows 11 in October 2021. As of October 2022, only 15.44% of PCs around the world run the new operating system (OS); 71.29% are ...
Xact IT Solutions

Cutting-edge strategies for cybersecurity success
Although cyberattacks on businesses have become increasingly prevalent in recent years, many small-business owners assume that their business is immune ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Don't Let Pranks Compromise Your Cybersecurity on April Fools' Day
April Fools' Day is known for pranks and practical jokes. Sadly, fraudsters frequently use this occasion to conduct attacks on unsuspecting victims. Here ...
Xact IT Solutions

Clearing the clutter on your Android device
If you’ve just bought a new Android device, there’s a good chance that it came pre-installed with some apps that you don’t want or need. Find out ...
Xact IT Solutions

It’s about time you use your Mac’s Time Machine
If you’re a Mac user, you probably already know that macOS boasts a remarkable built-in feature called Time Machine, which helps easily recover deleted ...
Xact IT Solutions

How to increase the life span of your business computer and hardware
If you rely heavily on computers for routine tasks in daily operations, making sure they keep running as smoothly and efficiently as possible is essential. ...
Xact IT Solutions

Cloud unified communications migration made simple: A comprehensive guide
Moving your unified communications (UC) system to the cloud offers global accessibility for your business operations. It allows you to manage your UC ...
Xact IT Solutions

Unlock the power of Workplace Analytics to achieve higher productivity
Imagine being able to monitor employee productivity, identify bottlenecks, and see where improvements could be made with a single business solution. ...
Xact IT Solutions

Crucial WordPress maintenance tasks to keep your site running smoothly
Are you unsure about the performance of your WordPress site? With just a few routine maintenance checks, you can ensure the security, safety, and optimal ...
Xact IT Solutions

Lift the burden of manual tasks with automation
For your business to get the most out of workflow automation, it is important to understand exactly what it is, how it works, and the benefits it offers. ...
Xact IT Solutions

Boost productivity and cut costs with Microsoft Exchange Online
Microsoft Exchange Server has long been the gold standard in enterprise-level email solutions, but many small businesses have shied away from it due ...
Xact IT Solutions

The five types of hackers targeting SMBs
Small- or medium-sized business (SMB) owners may think they’re unimportant enough to be targeted by hackers. But the truth is that SMBs are prime targets ...
Xact IT Solutions
XACT IT SOLUTIONS INC

We have a new National Cybersecurity Strategy, what does it mean?
In this 39-page document . . .
The Biden administration starts off by recognizing that cybersecurity is here to stay, that this is something that everybody ...
Xact IT Solutions

How to ensure the security of IoT devices in healthcare
With the widespread implementation of the Internet of Things (IoT) in healthcare, security concerns that were previously not considered have suddenly ...
Xact IT Solutions

6 Practical tips for strengthening device security
Many people don’t realize just how vulnerable today’s computers and mobile devices are to nosy individuals and cybercriminals. However, by taking ...
Xact IT Solutions

What Compliance Standards Does Your Business Need To Maintain?
Understanding HIPAA, NIST And CMMC
Compliance standards are some of the most important things a business needs to maintain to be profitable and well-respected ...
Xact IT Solutions
XACT IT SOLUTIONS INC

How to Choose the Best Co-managed IT Partner for your Business
Cyber threats are real and growing. And there is no sign of a decline in the near future. Are your organization's tools and technologies capable of protecting ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Stepping Up Your Cybersecurity with Defense in Depth (DiD)
Cybersecurity is a critical component of any organization or business. Threats to an organization's operations, data, and reputation evolve alongside ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Think like a Hacker: Get to know the hacking techniques and how to combat them
To evade security measures, cybercriminals are constantly exploring new tactics. Thus, it is crucial to adopt a hacker's mindset and employ preemptive ...
Xact IT Solutions

Signs your VoIP system has been compromised
Voice over Internet Protocol (VoIP) systems have many advantages over traditional telephone systems, but they also come with a unique set of risks. Because ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Building Resilient Defense Strategies Against Insider Threats
Insider threats are a serious concern in the realm of cybersecurity. Unfortunately, many organizations of all sizes either neglect or are hesitant to ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Top 4 Co-Managed IT Myths
As a business owner, you may be torn between relying solely on your internal IT staff or outsourcing to an IT service provider. But what if there was ...
Xact IT Solutions

Online tools every remote worker needs
Working in a virtual environment can be challenging for any team, but it doesn’t have to be. Using tools and technologies that allow distributed teams ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Does Your Business Need Co-Managed IT?
When considering how to handle the management of your business's IT infrastructure, there are various options available. One option is to opt for fully ...
Xact IT Solutions

Ways to ensure safe web browsing
Even the simple act of browsing the web can expose your employees to countless cyberthreats. And with the rise of remote and hybrid work setups, employees ...
Xact IT Solutions
Maximizing success: The benefits of regular technology business reviews to SMBs
If you’re running a small- or medium-sized business (SMB), then you know that managing your company’s IT system can be a real challenge. This is ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Everyone Is Getting Hacked, "Don't Pay The Ransom" FBIs Wray Says
In the news
The city administration of Oakland, California has declared a state of emergency due to various issues that they are facing after they have ...
Xact IT Solutions

Maximize Windows 11 performance: Top tips and tricks
If you’ve made the switch to Windows 11, then you are familiar with its new features, effects, and animations. You’ve also probably noticed that ...
Xact IT Solutions
ALLEN PAJAR

Factors to consider when buying antivirus software
Cyberattacks can come for any business, regardless of size or scope. Small- and mid-sized businesses, in particular, are facing an increasing risk from ...
Xact IT Solutions

Everything you need to know about mobile threat defense
The use of mobile devices skyrocketed in the latter half of the 2000s, so it was only a matter of time before hackers took advantage. To protect users ...
Xact IT Solutions

Protect your Mac from ransomware with these tips
Businesses and individuals alike rely on Macs for tasks that require a high level of security, such as online banking, shopping, and storing important ...
Xact IT Solutions

Managed IT services providers in healthcare: The top benefits
In a world increasingly dependent on technology, healthcare providers cannot afford to have outdated and inefficient systems. When people’s lives are ...
Xact IT Solutions
XACT IT SOLUTIONS INC
Hackers Unleashed ESXiArgs Ransomware on VMWare ESXi
The VMware ransomware ESXiArgs is spreading like wildfire through the internet right now, infecting thousands of servers across the globe. CISA has come ...
Xact IT Solutions

5 Creative and useful ideas for your old PC
It’s no secret that technology advances at a rapid pace. Sooner or later, even the best devices will start to feel slow and outdated. If you’re in ...
Xact IT Solutions

Open-source VoIP vs. proprietary VoIP: Which is best for your business?
Businesses looking for a Voice over internet protocol (VoIP) solution can choose from two options: open-source and proprietary systems. To help you decide ...
Xact IT Solutions
XACT IT SOLUTIONS INC
FBI takes down Hive ransomware group, saves businesses millions
I want to cover the news that just broke yesterday on January 26th, 2023, where it's been reported that the FBI, The Federal Bureau of Investigations ...
Xact IT Solutions

How Microsoft 365 can help your SMB grow
As the owner of a small- or medium-sized business (SMB), you may feel like you’re always stretched thin. You have to manage tight budgets, juggle multiple ...
Xact IT Solutions

Private browsing: How to stay safe online
Are you concerned that someone might come across your online search history? Do you want to go gift shopping without having anyone else find out? Or, ...
Xact IT Solutions

The importance of identity and access management in protecting your business
No matter how well you protect your business from cyberattacks, there is always a risk that someone will find a way to break in. That’s why it’s ...
Xact IT Solutions

How to perform a clean install of Windows 11
Performing a clean install of Windows 11 allows you to start fresh with a completely new operating system that is free of old settings, unnecessary files, ...
Xact IT Solutions

Don’t overlook your business printers’ security
The security of business printers is often overlooked by small- and medium-sized businesses (SMBs). This can prove to be a big mistake because printers ...
Xact IT Solutions

How to pick the right EMR system for your practice
Electronic medical records (EMRs) allow healthcare providers to keep patients’ health records in digital format, eliminating the need for paper charts ...
Xact IT Solutions

A simple way to improve your home Wi-Fi
To facilitate communication and collaboration among remote workforce, fast and reliable home Wi-Fi connections are essential. If you are a remote worker ...
Xact IT Solutions

Improve Your Cyber Security Awareness
Learn About Today’s Most Common Types Of Cyber-Attacks
If you’ve turned on the news sometime during the past few years, you’ve probably heard ...
Xact IT Solutions

Drive your business forward with these VoIP services
More and more companies are making the switch to Voice over Internet Protocol (VoIP) from traditional landlines due to VoIP’s cost-efficiency, cutting-edge ...
Xact IT Solutions

Explaining Microsoft 365 Groups Connectors
Microsoft 365 Groups connectors allow users to send messages and files to anyone in the group, regardless of whether they are using Outlook, SharePoint, ...
Xact IT Solutions

Utilize AI to grow your eCommerce business
eCommerce is enjoying a period of unprecedented growth, and its continued development shows no signs of stopping, thanks to artificial intelligence (AI) ...
Xact IT Solutions

Don’t let a power outage cripple your business — invest in a UPS
Power outages are a huge inconvenience to businesses. They can lead to lost productivity and revenue, and they can cost you a lot in damages. That’s ...
Xact IT Solutions

What’s new for Windows 11 in 2023
Windows 11 underwent various upgrades over the course of 2022, with the 22H2 update being the most significant. But what does 2023 have in store for ...
Xact IT Solutions

Cybersecurity trends that will shape the future of business
Businesses of all sizes can fall prey to cyberattacks that can cause major financial losses and even put companies out of business. And with more numerous ...
Xact IT Solutions

Your guide to reducing your Android’s data consumption
In recent years, mobile data consumption has soared. Today’s apps require extensive data resources and continually ask users to update them with newer ...
Xact IT Solutions

How to tell if your Mac has been infected with malware
Has your Mac been acting strangely lately? Are you seeing strange pop-ups or advertisements, or are your applications taking longer to load than usual? ...
Xact IT Solutions

Keep your work devices clean and running smoothly with these tips
It’s no secret that a clean work environment is more productive than a cluttered one. The same principle applies to your computer and mobile devices. ...
Xact IT Solutions

VoIP optimization tips: Don’t let the holidays overwhelm your business
If you don’t want to be overwhelmed with the influx of calls from customers this holiday season, it’s important to optimize your Voice over Internet ...
Xact IT Solutions
XACT IT SOLUTIONS INC
FTC Safeguard Rules: What You Need to Know
In June of 2023, the FTC Safeguard Rules go into affecting millions of businesses across the US. These businesses must implement cybersecurity or face ...
Xact IT Solutions

Give Your Business The Protection It Needs With Cyber Insurance
Being at risk for cyber-attacks is a growing concern among small-business owners. Cybercriminals often target small businesses because they hold sensitive ...
Xact IT Solutions
ALLEN PAJAR

Tips to help you master Microsoft Word and boost your productivity
Microsoft Word continues to be a popular office suite for many businesses because of its versatile features. It’s user-friendly and straightforward, ...
Xact IT Solutions

A quick guide to web hosting
To make your business visible to the world, you must establish an online presence. Doing so requires creating a website and partnering with a capable ...
Xact IT Solutions

Get your eCommerce business ready for the holiday rush
With the holidays fast approaching, now is the time for eCommerce companies to start planning and preparing for increased traffic and sales. However, ...
Xact IT Solutions

Speed up your computer in minutes with this simple tool
Did you know? Your Windows computer accumulates files over time, and this can slow down its performance. But don’t fret. You can speed up your computer ...
Xact IT Solutions

How to choose the right VPN for your business
If you want to stay secure while using the internet, it’s not enough to simply rely on anti-malware software and a firewall. Nowadays, hackers can ...
Xact IT Solutions

Crucial tips to protect customers’ PHI
If your business handles protected health information (PHI), it’s your duty to take every step possible to ensure that your clients’ data is secured. ...
Xact IT Solutions

Wi-Fi not working? Here are fixes to the most common connection issues
Although we now enjoy much faster internet speeds and improved Wi-Fi reliability in comparison to years past, Wi-Fi technology isn’t perfect. Here ...
Xact IT Solutions
XACT IT SOLUTIONS INC

3 Quick Things To Do Before You Head Out For The Holidays
Chances are you and your employees are taking some well-deserved time off in the next few weeks. As a business owner or executive, you may find it ...
Xact IT Solutions

Protect your VoIP system with these security measures
If your business uses Voice over Internet Protocol (VoIP), it’s important to make sure that your data is safe and secure. Luckily, there are many security ...
Xact IT Solutions
Get rid of presentation jitters with PowerPoint Presenter Coach
If you want to improve your online presentation skills, such as body language and speaking, PowerPoint Presenter Coach can give you instant feedback ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Rackspace Hosted Exchange Down Due to Security Incident
Today, we are going to discuss what is going on over at Rackspace. Over the weekend, another cloud provider, and in this case, it happened to be companies, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

4 Core Benefits of Cloud Backup for SaaS Platforms
Businesses like yours are increasingly adopting cloud-based solutions to keep up with the rapidly changing technological landscape. According to a recent ...
Xact IT Solutions

How to boost website conversion
If you want your website to achieve success, then you need to focus on conversions rather than simply website traffic. Without any conversion rates, ...
Xact IT Solutions

The 3 biggest disaster recovery myths that businesses should ignore
Disaster recovery (DR) has undergone major changes for the better since cloud computing became popular. In particular, small- and medium-sized businesses ...
Xact IT Solutions

How Microsoft Loop can boost your productivity
Microsoft Loop is a new app that promises to help boost your productivity. It combines a powerful and flexible canvas with portable components that stay ...
Xact IT Solutions
XACT IT SOLUTIONS INC
Are Your Smart Devices (Siri, Alexa, Google) Eavesdropping On You?
Have you ever had a conversation about a topic, and then later that day you start seeing news, ads or updates about that subject, and said to yourself, ...
Xact IT Solutions

Top tips to protect yourself from holiday hackers
As you focus on meeting the needs of holiday shoppers or taking time off to be with loved ones, hackers are looking to exploit any vulnerabilities in ...
Xact IT Solutions

What you can do with the combined power of Android and Google
Google offers several features to help you stay organized and make the most of your digital life. One of these is being able to sync across devices, ...
Xact IT Solutions

Helpful tips for connecting your Mac to an external monitor
If you want to be more productive on your Mac, adding a second monitor is the best solution. You’ll be able to work on large spreadsheets and compare ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Top 5 Threats IoT Devices Pose to Data Protection & Privacy
Gartner Inc. predicted that by 2023, CIOs would be responsible for over three times the endpoints they were responsible for in 2018 due to the rapid evolution ...
Xact IT Solutions

Give Your Business An Advantage In 2023 Prepare Your Business For A Successful 2023 With These 3 New Year’s Tech Resolutions
If you don’t have goals for 2023, there’s no better time than the first month of the year to make them. Whether you want to increase sales, customer ...
Xact IT Solutions

Advantages of dual monitor systems
Dual monitor systems can be great investments for your small business. By using two monitors, you and your employees can increase your productivity and ...
Xact IT Solutions
XACT IT SOLUTIONS INC

What is Ransomware?
In today’s blog, we will be going into something that most people seem to have basic or common knowledge, but you'd be surprised of how many people ...
Xact IT Solutions

How to keep your VoIP systems safe
While investing in Voice over Internet Protocol (VoIP) systems is known to help businesses reduce their telecommunication costs, failing to secure these ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Make Purchases Online? Here Are 4 Things You (And Your Employees) Need To Do To Keep From Becoming A Prime Target For Cybercriminals
ROI Revolution estimates that e-commerce sales will eclipse $236 billion this holiday season. While that’s the most popular time for consumers to ...
Xact IT Solutions

Microsoft 365 Defender: Protecting users from phishing attacks
Microsoft 365 Defender is a powerful cybersecurity tool that helps protect users from phishing attacks. In this blog post, we will discuss how Microsoft ...
Xact IT Solutions

How much internet bandwidth do you really need to work remotely?
If your company shifted to a remote work setup, you should understand how crucial having enough internet bandwidth for remote workers is. But what does ...
Xact IT Solutions

What to consider when selecting an MSP
When it comes to running their company, one thing business owners often overlook is IT management. This is because they mistakenly assume they can handle ...
Xact IT Solutions
XACT IT SOLUTIONS INC

If You Have Employees Working From Home, Here Are Three Things All Remote Employees Must Do Now To Prevent Your Company From Being Hacked
The last few years have seen countless companies going to a hybrid work model. According to a survey by Envoy over 77% of businesses have some full or ...
Xact IT Solutions

Tips for removing bloatware from your Windows 11 PC
New Windows 11 laptops and desktops may sometimes come with bloatware. While you can uninstall some of them, others require more effort to get rid of. ...
Xact IT Solutions

Ramp up your defenses with proactive cybersecurity
Cyberthreats are becoming more sophisticated every day, and if your business isn’t taking steps to protect itself from these threats, it faces a high ...
Xact IT Solutions

Can big data lower hospital readmission rates?
Business intelligence (BI) refers to the process of gathering data and turning it into useful insights. This data can be used to make better decisions ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Why Your Business Needs a Data Security Policy
Today, the competitive business environment is data-driven. Data provides key insights into your customers and business performance that helps you make ...
Xact IT Solutions

A guide to choosing the perfect mouse for you
How do you know which mouse to buy when there are so many options on the market? In this guide, we will provide some tips on how to find the perfect ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Regulations & Reputations: How Compliant Is Your Supply Chain?
With both technology and tech-related threats evolving faster than ever before, supply chain risks have taken on a new meaning in today’s digital world. ...
Xact IT Solutions

How to minimize VoIP downtime and keep your business connected
Voice over Internet Protocol (VoIP) telephony systems are one of the most essential technologies for businesses today. If your VoIP system goes down, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

How Insiders Pose a Serious Threat to Your Business-Critical Data
Merely mitigating external cybersecurity threats isn’t enough to fight cybercrime in today’s ever-evolving threat landscape. Although insider threats ...
Xact IT Solutions

These new Microsoft 365 features help support hybrid workers
Hybrid work is quickly becoming the norm, and Microsoft has responded to this shift by improving Microsoft 365 to address the challenges that come with ...
Xact IT Solutions

Give Your Business An Advantage In 2023 By Paying Attention To Important IT News And Trends Of 2022
The year 2022 was a big one for IT, experiencing growth in all areas, especially for infrastructure in remote work due to the pandemic. When businesses ...
Xact IT Solutions

Gmail productivity tips you should know
A study done by the McKinsey Global Institute found that employees spend an average of 13 hours every week checking their emails. You can bring that ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Fines, Penalties and Violations! Oh My!
Global data protection regulations (new or updated) are being enforced aggressively, resulting in a tsunami of hefty fines and penalties handed out to ...
Xact IT Solutions

Be prepared for disasters: Business continuity planning for SMBs
A major crisis can happen to any business, at any time, so it’s important to be prepared for when things go wrong. One way to do this is by creating ...
Xact IT Solutions

Microsoft Edge: 9 Most useful features
There are plenty of reasons why Microsoft Edge is a great choice for professionals: its speed, security, and compatibility with Microsoft Office make ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Strengthen Your IT & Data Security to Prevent Cyberattacks
The COVID-19 pandemic has changed everything about the world as we know it. Just as we started embracing new practices like sanitizing, social distancing ...
Xact IT Solutions

Update your passwords now
If you’re like most people, you probably have passwords that are easy to remember or use the same one for multiple accounts. But by doing either of ...
Xact IT Solutions

Android accessories to take your smartphone use to the next level
If you’ve got a new Android phone and are looking for something classy and trendy to go with it, or if you’re trying to find the perfect gift for ...
Xact IT Solutions

Keep your iPhone text messages private with these tips
If you’re a business owner who relies on text messages to communicate with employees, clients, or customers, it’s essential to ensure the privacy ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Why Passwords are Your Business’s Weakest Point
In today's digital world, safeguarding your organization's online assets is critical. Unfortunately, poor password hygiene practices by some employees ...
Xact IT Solutions

Why your company should care about HIPAA compliance
If your organization handles sensitive patient information, you need to comply with HIPAA. Failure to do so can result in fines and penalties. Read on ...
Xact IT Solutions
What is firmware and why is it important?
Securing your small business is a never-ending battle, but there are some steps you can take to make it a little bit easier. One of those steps is making ...
Xact IT Solutions

What are the costs associated with owning a VoIP system?
Voice over Internet Protocol (VoIP) systems are a more cost-effective alternative to traditional phone systems. For a fixed monthly bill, you get enterprise-grade ...
Xact IT Solutions

Streamline your schedule with Microsoft 365
Microsoft 365 is chock-full of features that can help businesses stay organized and connected. One of these is the ability to share calendars with co-workers. ...
Xact IT Solutions
XACT IT SOLUTIONS INC

PCI-DSS Compliance: What You Should Know
Over the last year, many organizations struggled to keep their private data secure against cyberthreats as they rushed to adapt to pandemic-inspired ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Busting Four Popular Cybersecurity Myths
As the business world becomes increasingly digitized, you’ll have to tackle several dangers that come with doing business online. Cybercriminals nowadays ...
Xact IT Solutions

What is single sign-on and why should you be using it
If you use multiple applications and accounts for work, you know how frustrating it can be to have to enter different usernames and passwords for each ...
Xact IT Solutions

Avoid these 5 common IT investment mistakes
Investing in new technology is a great way to drive business growth. For instance, purchasing new servers can boost your employees’ ability to multitask ...
Xact IT Solutions

What you need to know about the new Windows 11 update
The long-anticipated Windows 11 2022 update, or Windows 11 version 22H2, has now been released. This upgrade was the result of a year of development ...
Xact IT Solutions
XACT IT SOLUTIONS INC

I.T. Support Philadelphia - 3 Red Flags You're Being Underserved
Not all I.T. Support in Philadelphia is created equal - 3 Red Flags You're Being Underserved
Hey everyone, it's Bryan Hornung, CEO of Xact IT Solutions, ...
Xact IT Solutions

Do I Need To Upgrade My Network? 4 Amazing Benefits You’ll Experience
A business owner has many responsibilities within their business. They can be so busy that sometimes things are overlooked for an extended period of ...
Xact IT Solutions

7 Ways to keep your email account safe
Email is one of the most essential business tools today. It enables swift, efficient communication within a company and with their customers and partners. ...
Xact IT Solutions

Are EHR systems better than paper-based systems?
Healthcare companies now realize that paper-based medical records have more drawbacks than advantages, and that it’s time to switch to electronic health ...
Xact IT Solutions

BYOD and CYOD: What can they do for your business?
When it comes to choosing the right work device policy for your business, you will likely come across two options: bring your own device (BYOD) and choose ...
Xact IT Solutions

The benefits of call recording: Get more from your conversations
Recording phone calls is a common practice for many businesses. It allows them to analyze customer sentiment, track employee performance, and measure ...
Xact IT Solutions

Microsoft 365 data security: 7 Ways to boost protection
Microsoft 365 has become an incredibly popular choice for enterprises of all sizes looking for a comprehensive set of tools for staying productive and ...
Xact IT Solutions
XACT IT SOLUTIONS INC

3 Types of Cyber Insurance You Need to Know About
As the world becomes more digitized and cybercrime increases, the need for cyber insurance is something businesses should not overlook. If your company ...
Xact IT Solutions

Make your website stand out with these modern design trends
Nearly 94% of a visitor’s first impression of your business comes from web design. That’s why it’s critical that your website uses modern web design ...
Xact IT Solutions

The advantages of using a cloud-based OMS
In today’s business world, having a cloud-based OMS can give you a big advantage. The cloud offers many benefits, including the ability to access your ...
Xact IT Solutions
Here’s how to remove unwelcome notifications in Windows 11
Don’t be surprised if you see some ads while using your Windows 11 computer. Microsoft designed its operating systems to show notifications and ads, ...
Xact IT Solutions
XACT IT SOLUTIONS INC

Don’t Fall for These Cyber Insurance Myths
As the world increasingly moves online, so do the risks to our businesses. Cyber insurance is one way to help your business recover following a cyberattack. ...
Xact IT Solutions

Defending against watering hole attacks
More and more cybercriminals are launching watering hole attacks to gain access to company networks. But what exactly is a watering hole attack, and ...
Xact IT Solutions

Hassle-free ways to transfer files from Android to PC or Mac
You may want to transfer files from your Android phone to a PC or Mac to back up your files and free up some storage space on your device. Thanks to ...


